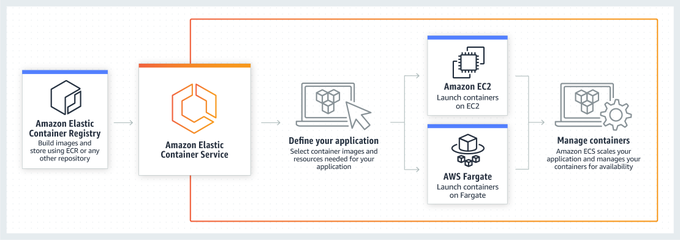
More from Software
buffalo uses dominion scoreboard software so not really
DEAD PEOPLE SCORED FOR BUFFALO!
A truck delivered off a suitcase full of points at halftime from Canada for Buffalo.
#StopTheSteel !!!!
I’ll be submitting sworn affidavits from Steelers fans than they saw the Buffalo rigging the game but I want to emphasize that I’m not under oath.
Sports Minute: Bills improve to 10-3 with 26-15 win over sloppy Steelers https://t.co/lg0isTiE92
— Erie News Now (@ErieNewsNow) December 14, 2020
DEAD PEOPLE SCORED FOR BUFFALO!
A truck delivered off a suitcase full of points at halftime from Canada for Buffalo.
#StopTheSteel !!!!
I’ll be submitting sworn affidavits from Steelers fans than they saw the Buffalo rigging the game but I want to emphasize that I’m not under oath.
Are you a Designer or a Developer?👨💻
Here are some Google Chrome extensions that can make you better in 2021. 🔥🍀
(Thread) 🧵👇
1. https://t.co/zGir5E5U0J: https://t.co/PVx1wlX0Se is the easiest way to stay updated on the latest programming news. Get the hottest dev news from the best tech blogs on any topic you can think of.
2. CSS Peeper: CSS Peeper is a CSS viewer tailored for Designers. Get access to useful styles with our Chrome extension. Its mission is to let Designers focus on design, and spend as little time as possible digging in a
3. UX Check: UX Check makes heuristic evaluations quick and easy. The extension will open up Nielsen's Ten Heuristics in a side pane next to your website.
4. Checkbot: Checkbot finds critical SEO, speed & security problems before your website visitors do
Tests 100s of pages at once for broken links, duplicate titles, invalid HTML, insecure pages, and 50+ other
Here are some Google Chrome extensions that can make you better in 2021. 🔥🍀
(Thread) 🧵👇
1. https://t.co/zGir5E5U0J: https://t.co/PVx1wlX0Se is the easiest way to stay updated on the latest programming news. Get the hottest dev news from the best tech blogs on any topic you can think of.
2. CSS Peeper: CSS Peeper is a CSS viewer tailored for Designers. Get access to useful styles with our Chrome extension. Its mission is to let Designers focus on design, and spend as little time as possible digging in a
3. UX Check: UX Check makes heuristic evaluations quick and easy. The extension will open up Nielsen's Ten Heuristics in a side pane next to your website.
4. Checkbot: Checkbot finds critical SEO, speed & security problems before your website visitors do
Tests 100s of pages at once for broken links, duplicate titles, invalid HTML, insecure pages, and 50+ other