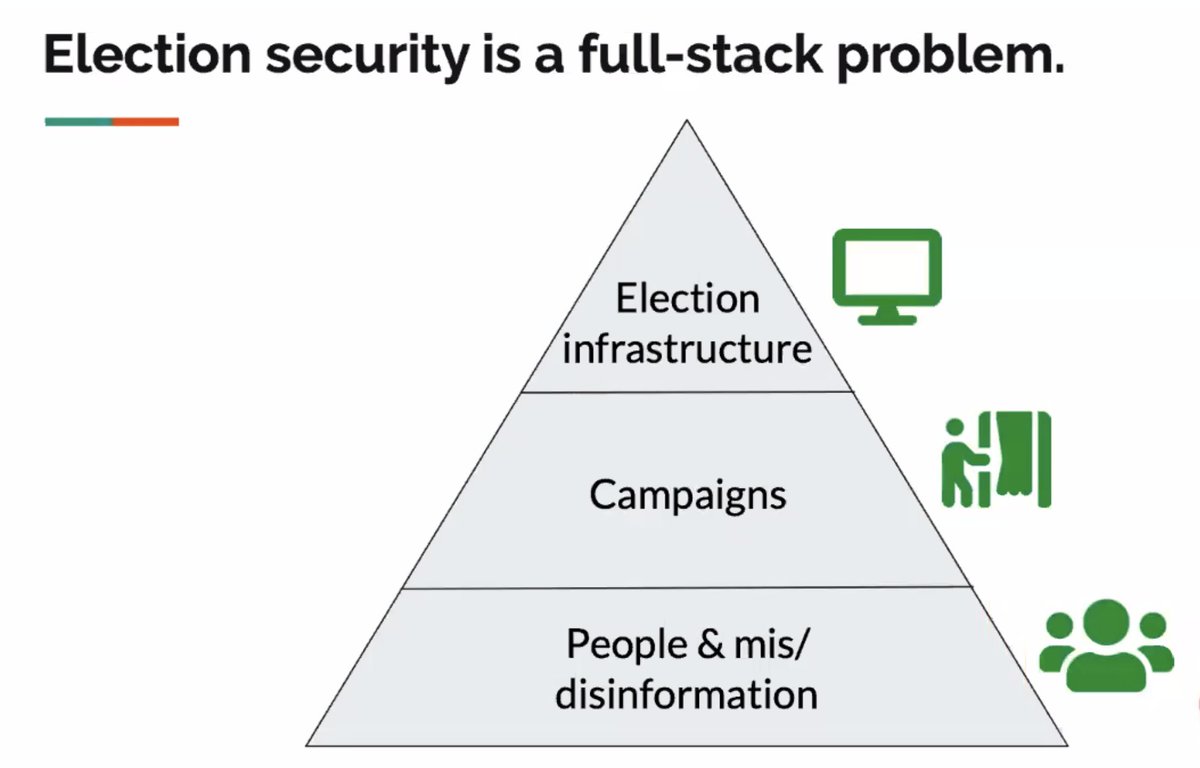
Next up at #enigma2021, Sanghyun Hong will be speaking about "A SOUND MIND IN A VULNERABLE BODY: PRACTICAL HARDWARE ATTACKS ON DEEP LEARNING"
(Hint: speaker is on the
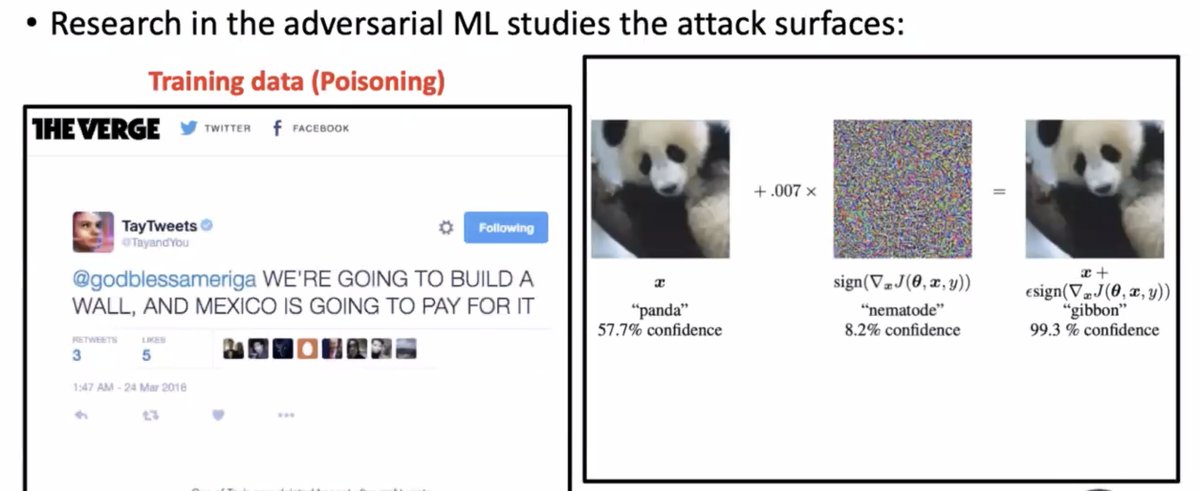
* looks at the robustness in an isolated manner
* doesn't look at the whole ecosystem and how the model is used -- ML models are running in real hardware with real software which has real vulns!
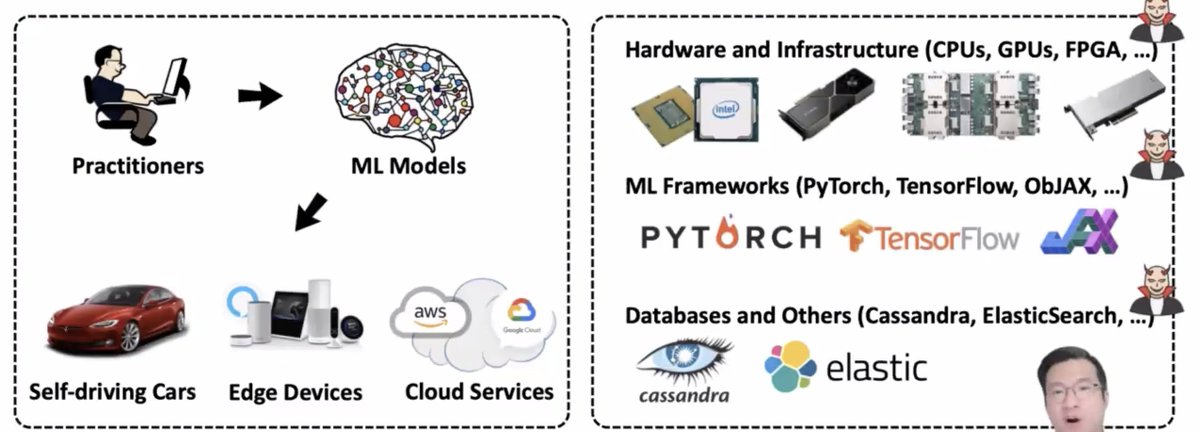
e.g. fault injection attacks, side-channel attacks
* co-location of VMs from different users
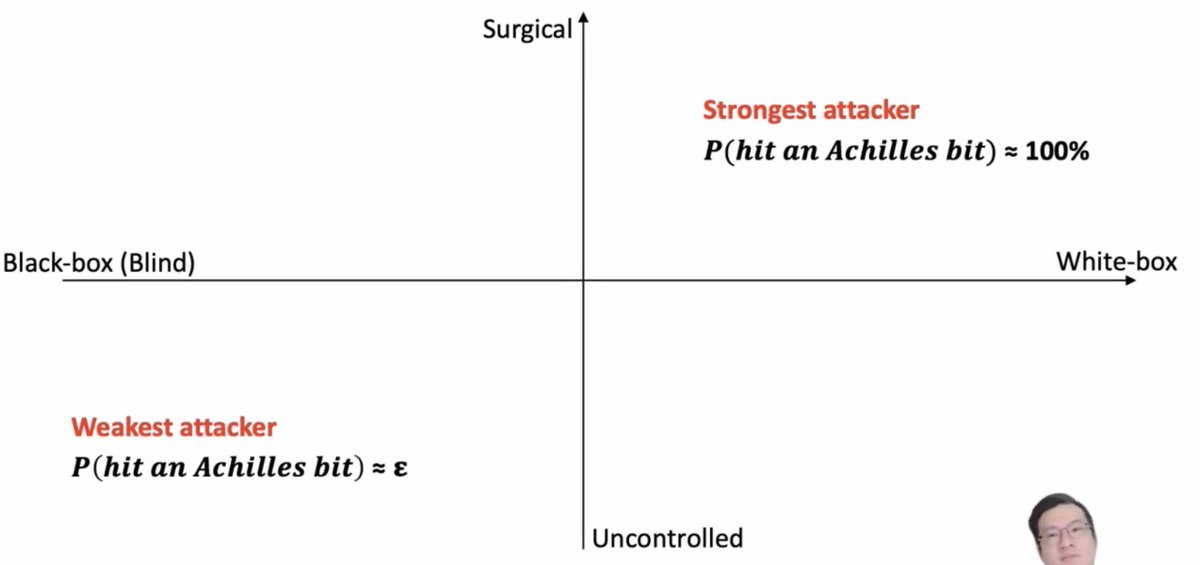
* weak attackers with less subtle control
The cloud providers try to secure things, e.g. protections against Rowhammer
... BUT this focuses on the average or best case, not the worst cast!
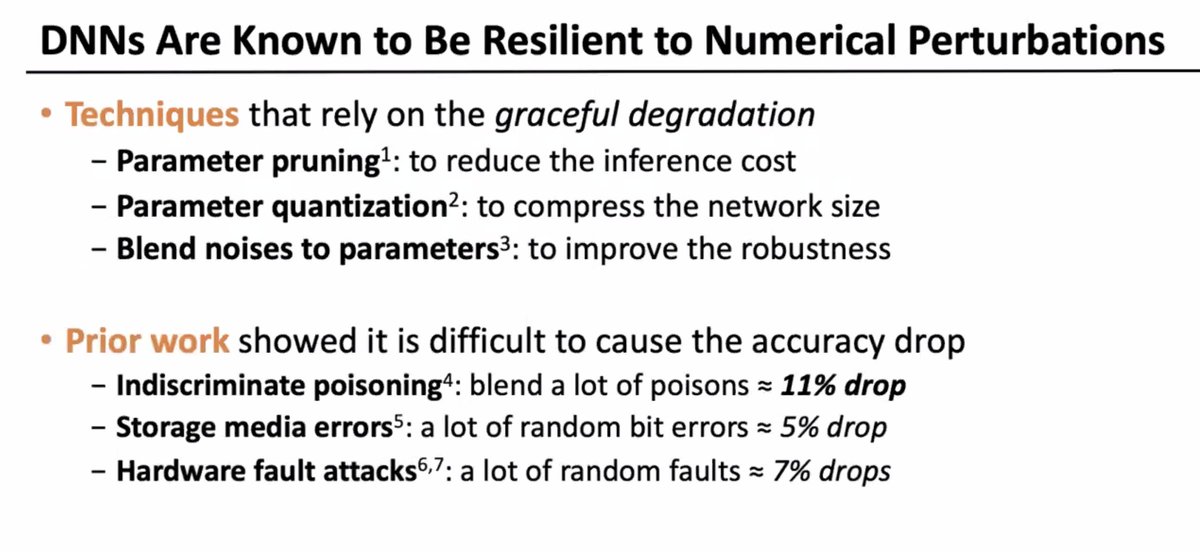
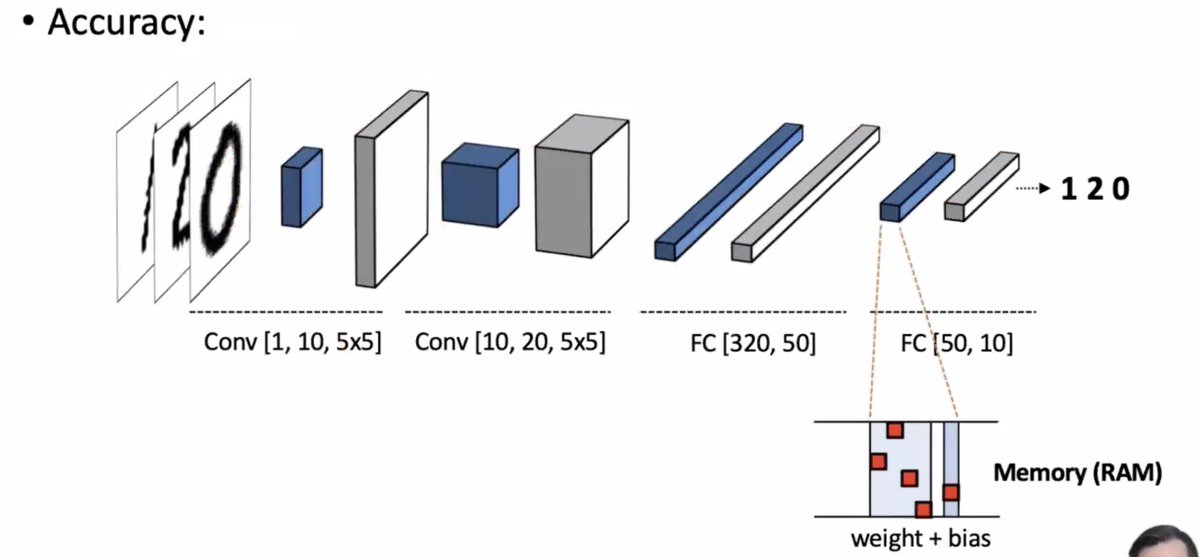
* negligible effect on the average case accuracy
* but flipping one bit can make significant amount of damage for particular queries
How much damage can a single bit flip cause?
Some strong attackers might be able to hit an "achilles" bit (one that's really going to mess with the model), but weaker attackers are going to hit bits more randomly.
The attacker might want to get their hands on fancy DNNs which are considered trade secrets and proprietary to their creators. They're expensive to make! They need good training data! People want to protect them!
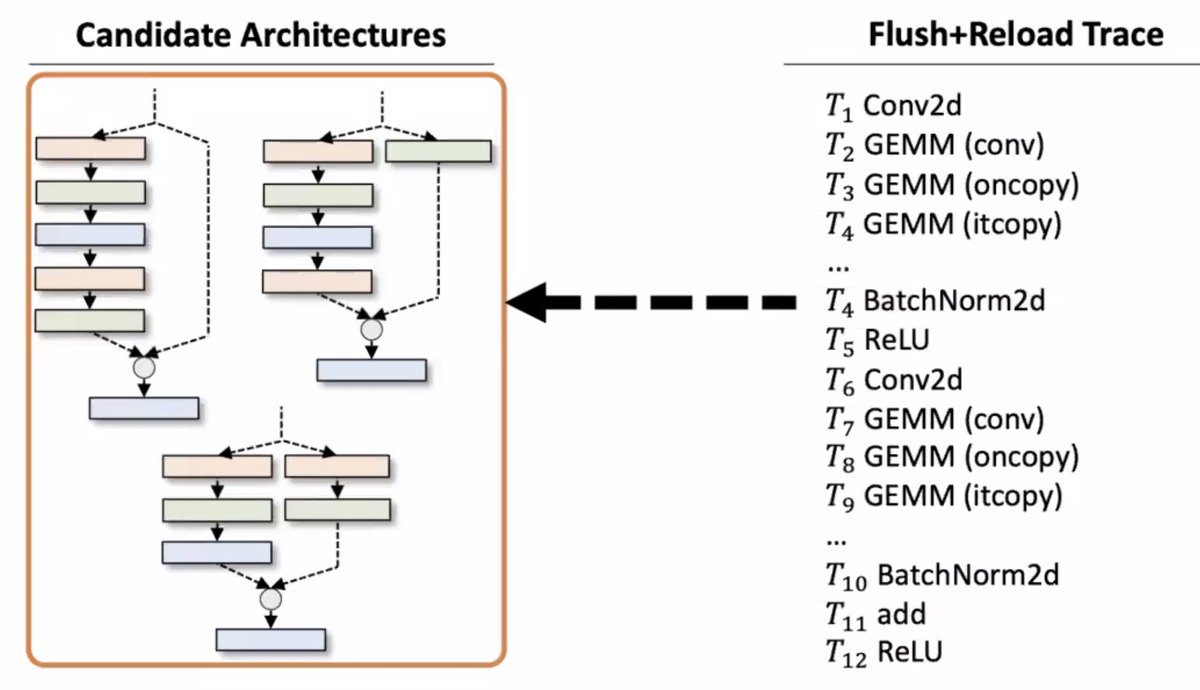
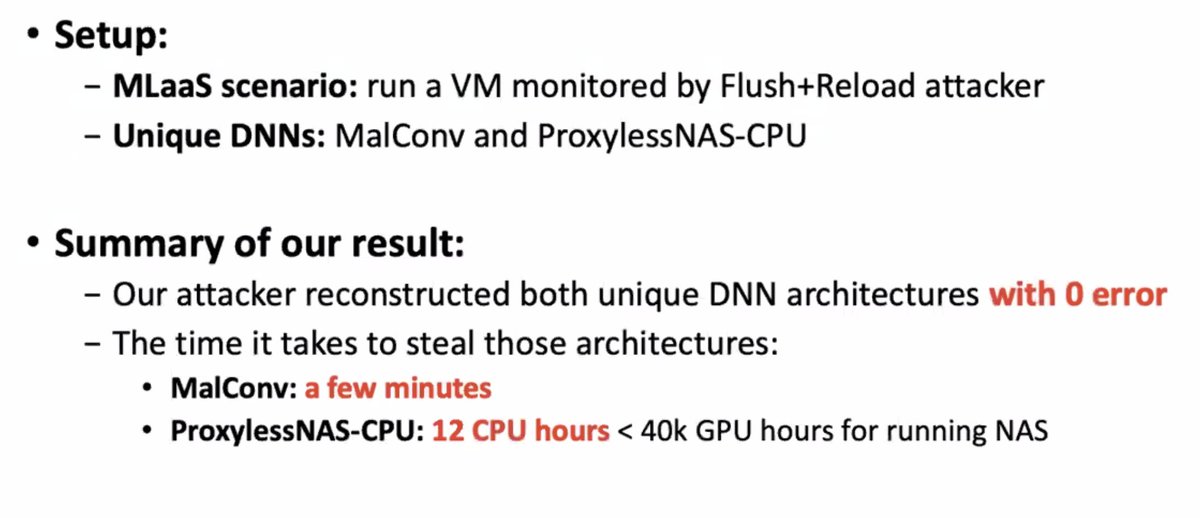
Does this work? Apparently so: they tried it out using a cache side-channel attack and got back the architectures of the fancy DNN back.
More from Lea Kissner
More from Science
You May Also Like
Funny, before the election I recall lefties muttering the caravan must have been a Trump setup because it made the open borders crowd look so bad. Why would the pro-migrant crowd engineer a crisis that played into Trump's hands? THIS is why. THESE are the "optics" they wanted.
This media manipulation effort was inspired by the success of the "kids in cages" freakout, a 100% Stalinist propaganda drive that required people to forget about Obama putting migrant children in cells. It worked, so now they want pics of Trump "gassing children on the border."
There's a heavy air of Pallywood around the whole thing as well. If the Palestinians can stage huge theatrical performances of victimhood with the willing cooperation of Western media, why shouldn't the migrant caravan organizers expect the same?
It's business as usual for Anarchy, Inc. - the worldwide shredding of national sovereignty to increase the power of transnational organizations and left-wing ideology. Many in the media are true believers. Others just cannot resist the narrative of "change" and "social justice."
The product sold by Anarchy, Inc. is victimhood. It always boils down to the same formula: once the existing order can be painted as oppressors and children as their victims, chaos wins and order loses. Look at the lefties shrieking in unison about "Trump gassing children" today.
Funny there are those who think these migrant caravans were a FANTASTIC idea that's going to take the immigration issue away from you.
— Brian Cates (@drawandstrike) November 26, 2018
Like several weeks watching a rampaging horde storm the fences & throw rocks at our border patrol agents & getting gassed = great optics!
This media manipulation effort was inspired by the success of the "kids in cages" freakout, a 100% Stalinist propaganda drive that required people to forget about Obama putting migrant children in cells. It worked, so now they want pics of Trump "gassing children on the border."
There's a heavy air of Pallywood around the whole thing as well. If the Palestinians can stage huge theatrical performances of victimhood with the willing cooperation of Western media, why shouldn't the migrant caravan organizers expect the same?
It's business as usual for Anarchy, Inc. - the worldwide shredding of national sovereignty to increase the power of transnational organizations and left-wing ideology. Many in the media are true believers. Others just cannot resist the narrative of "change" and "social justice."
The product sold by Anarchy, Inc. is victimhood. It always boils down to the same formula: once the existing order can be painted as oppressors and children as their victims, chaos wins and order loses. Look at the lefties shrieking in unison about "Trump gassing children" today.