Yesterday I did a thread on how Huawei is trying to manipulate Belgian policy audiences with a fake online ecosystem ahead of a key 5G decision. (https://t.co/ViIp7X5KsN) Huawei did not take kindly to my research.
So here's the thread on Huawei I promised yesterday. It seems Huawei is using social media black ops tactics to try to convince policy-makers in Belgium that it can be trusted to build 5G networks. \U0001f928 pic.twitter.com/noZKM13RuD
— Michiel van Hulten (@mvanhulten) December 22, 2020


Totally agree. Seems like a total fake account. For a person with 800k followers with an account created in only 9 months ago, one would expect that it would be a very important or famous person. But a news search with his name is rather disappointing.
— Javier Villaraco \U0001f3f3\ufe0f\u200d\U0001f308 (@villaraco) December 22, 2020

Enjoy~https://t.co/M7IntqNMjG
— Mike BAI (@Mike_IMC) December 22, 2020

Ik zat al een tijdje op dit dossier, maar gisteren gescooped door @mvanhulten die parallel hetzelfde uitzocht.
— Arbiter (@ArbiterOfTweets) December 23, 2020
De echte publicatieprimeur komt echter van @bickylover - volg die man! - die er zondag al een draadje over publiceerde. Dat kan je hier lezen:https://t.co/m0b8znc4mf
More from Crime
Once one party allows the pardon power to become a tool of criminal enterprise, its danger to democracy outweighs its utility as an instrument of justice.
— Chris Murphy (@ChrisMurphyCT) December 24, 2020
It\u2019s time to remove the pardon power from the Constitution.
In part because the Congress of which he is a part has established no functioning second-look mechanisms for shortening sentences or expunging convictions, commutations and pardons are the only mechanisms for correcting injustices in the federal system. /2
And it's not as if those injustices are rare. Go to any federal correctional facility, and take time to learn who is there and about their cases, and you find literally thousands of people whose sentences were grossly excessive given their offenses. /3
Those people need commutations as a corrective because there is no parole or other second look in place to address that. Some have tried to use compassionate release under the First Step Act, but DOJ tries to block those efforts at every turn and it's a limited option. /4
Presidential commutations are thus the only avenue for these folks. And under President Obama, more than 1,700 regular people (not his cronies) received relief. It was woefully inadequate for the need, but it shows the value of the power. /5
You May Also Like
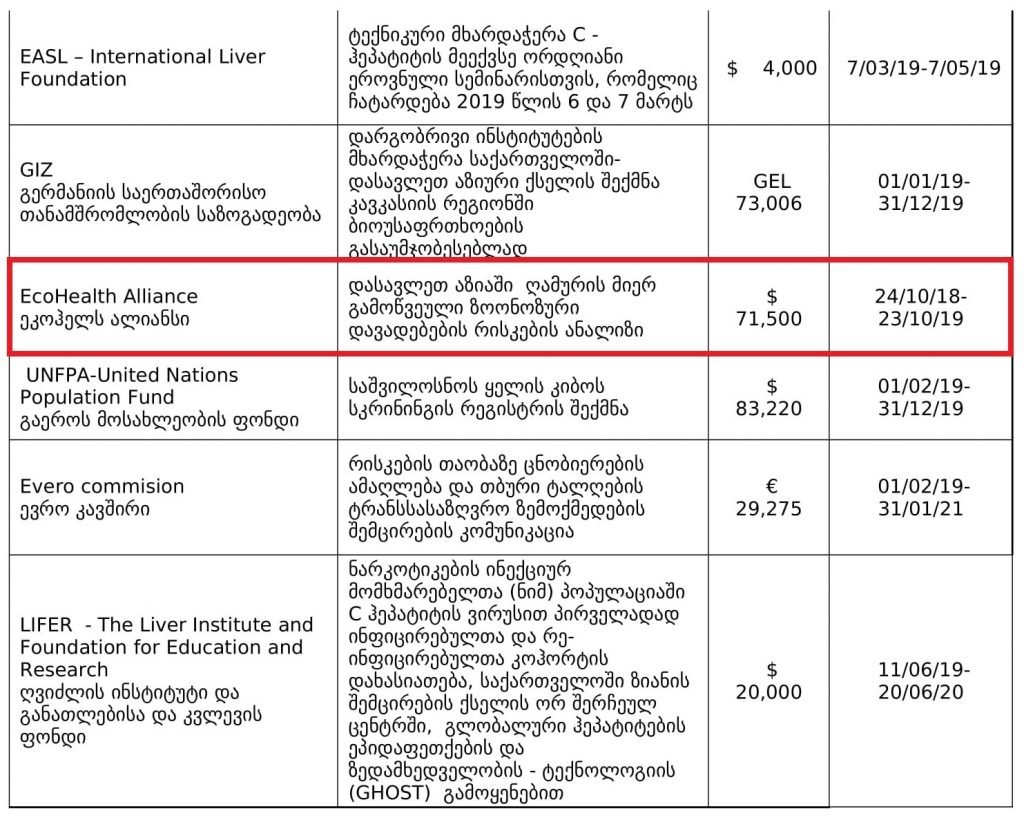
Risks of bat-borne zoonotic diseases in Western Asia
Duration: 24/10/2018-23 /10/2019
Funding: $71,500
@dgaytandzhieva
https://t.co/680CdD8uug
2. Bat Virus Database
Access to the database is limited only to those scientists participating in our ‘Bats and Coronaviruses’ project
Our intention is to eventually open up this database to the larger scientific community
https://t.co/mPn7b9HM48
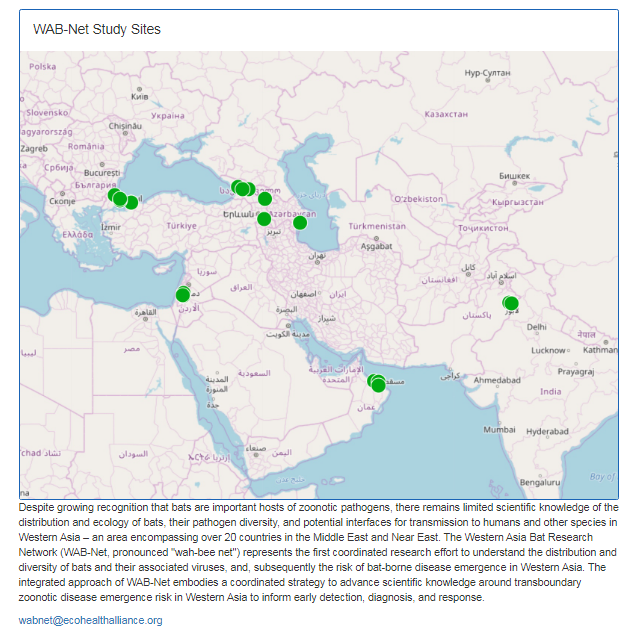
3. EcoHealth Alliance & DTRA Asking for Trouble
One Health research project focused on characterizing bat diversity, bat coronavirus diversity and the risk of bat-borne zoonotic disease emergence in the region.
https://t.co/u6aUeWBGEN

4. Phelps, Olival, Epstein, Karesh - EcoHealth/DTRA
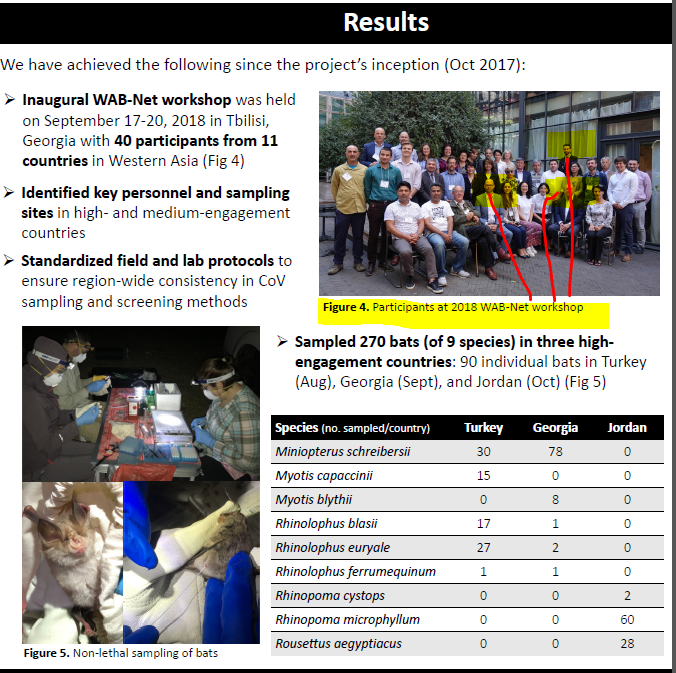
5, Methods and Expected Outcomes
(Unexpected Outcome = New Coronavirus Pandemic)

Funny there are those who think these migrant caravans were a FANTASTIC idea that's going to take the immigration issue away from you.
— Brian Cates (@drawandstrike) November 26, 2018
Like several weeks watching a rampaging horde storm the fences & throw rocks at our border patrol agents & getting gassed = great optics!
This media manipulation effort was inspired by the success of the "kids in cages" freakout, a 100% Stalinist propaganda drive that required people to forget about Obama putting migrant children in cells. It worked, so now they want pics of Trump "gassing children on the border."
There's a heavy air of Pallywood around the whole thing as well. If the Palestinians can stage huge theatrical performances of victimhood with the willing cooperation of Western media, why shouldn't the migrant caravan organizers expect the same?
It's business as usual for Anarchy, Inc. - the worldwide shredding of national sovereignty to increase the power of transnational organizations and left-wing ideology. Many in the media are true believers. Others just cannot resist the narrative of "change" and "social justice."
The product sold by Anarchy, Inc. is victimhood. It always boils down to the same formula: once the existing order can be painted as oppressors and children as their victims, chaos wins and order loses. Look at the lefties shrieking in unison about "Trump gassing children" today.
🗓 Release date: October 30, 2018
📝 New Emojis: 158
https://t.co/bx8XjhiCiB

New in iOS 12.1: 🥰 Smiling Face With 3 Hearts https://t.co/6eajdvueip

New in iOS 12.1: 🥵 Hot Face https://t.co/jhTv1elltB

New in iOS 12.1: 🥶 Cold Face https://t.co/EIjyl6yZrF

New in iOS 12.1: 🥳 Partying Face https://t.co/p8FDNEQ3LJ

It was Ved Vyas who edited the eighteen thousand shlokas of Bhagwat. This book destroys all your sins. It has twelve parts which are like kalpvraksh.
In the first skandh, the importance of Vedvyas

and characters of Pandavas are described by the dialogues between Suutji and Shaunakji. Then there is the story of Parikshit.
Next there is a Brahm Narad dialogue describing the avtaar of Bhagwan. Then the characteristics of Puraan are mentioned.
It also discusses the evolution of universe.( https://t.co/2aK1AZSC79 )
Next is the portrayal of Vidur and his dialogue with Maitreyji. Then there is a mention of Creation of universe by Brahma and the preachings of Sankhya by Kapil Muni.
HOW LIFE EVOLVED IN THIS UNIVERSE AS PER OUR SCRIPTURES.
— Anshul Pandey (@Anshulspiritual) August 29, 2020
Well maximum of Living being are the Vansaj of Rishi Kashyap. I have tried to give stories from different-different Puran. So lets start.... pic.twitter.com/MrrTS4xORk
In the next section we find the portrayal of Sati, Dhruv, Pruthu, and the story of ancient King, Bahirshi.
In the next section we find the character of King Priyavrat and his sons, different types of loks in this universe, and description of Narak. ( https://t.co/gmDTkLktKS )
Thread on NARK(HELL) / \u0928\u0930\u094d\u0915
— Anshul Pandey (@Anshulspiritual) August 11, 2020
Well today i will take you to a journey where nobody wants to go i.e Nark. Hence beware of doing Adharma/Evil things. There are various mentions in Puranas about Nark, But my Thread is only as per Bhagwat puran(SS attached in below Thread)
1/8 pic.twitter.com/raHYWtB53Q
In the sixth part we find the portrayal of Ajaamil ( https://t.co/LdVSSNspa2 ), Daksh and the birth of Marudgans( https://t.co/tecNidVckj )
In the seventh section we find the story of Prahlad and the description of Varnashram dharma. This section is based on karma vaasna.
#THREAD
— Anshul Pandey (@Anshulspiritual) August 12, 2020
WHY PARENTS CHOOSE RELIGIOUS OR PARAMATMA'S NAMES FOR THEIR CHILDREN AND WHICH ARE THE EASIEST WAY TO WASH AWAY YOUR SINS.
Yesterday I had described the types of Naraka's and the Sin or Adharma for a person to be there.
1/8 pic.twitter.com/XjPB2hfnUC