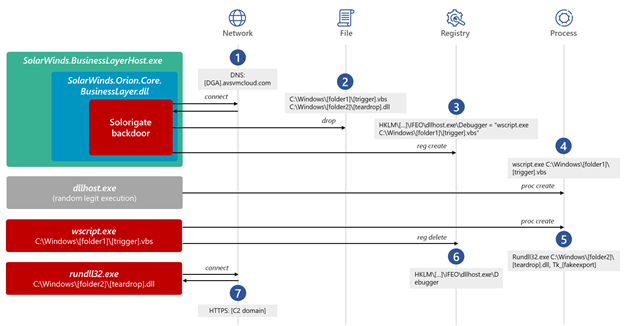
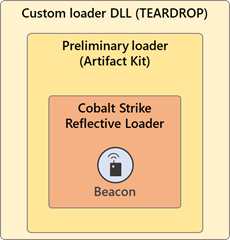
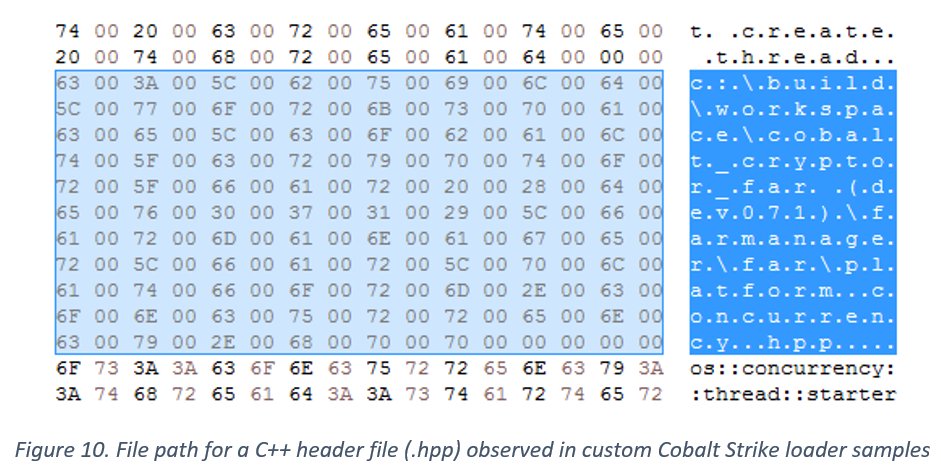
The missing link between the Solorigate backdoor and the custom #CobaltStrike loaders observed during the #Solorigate is an Image File Execution Options (IFEO) Debugger registry value created for the legitimate process dllhost.exe (ATT&CK ID: T1546.012).
As part of our commitment to keeping our customers/community protected & informed, we are releasing a blog that shines light on transition between Stage 1 and 2 of #Solorigate/#SUNBURST campaign, custom Cobalt Strike loaders, post-exploit. artifacts, IOCs: https://t.co/b0ReHMa63u
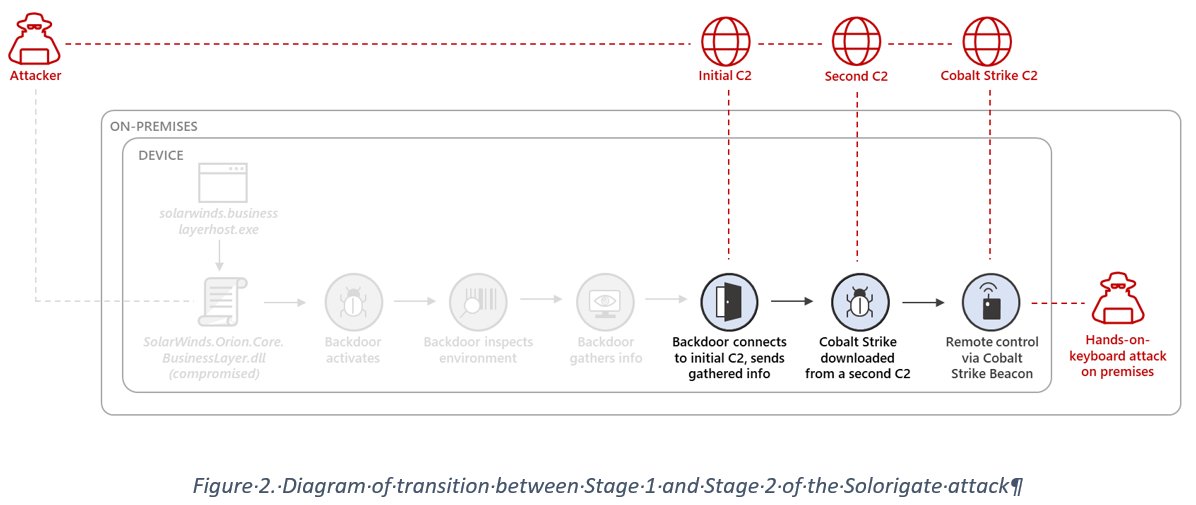
The missing link between the Solorigate backdoor and the custom #CobaltStrike loaders observed during the #Solorigate is an Image File Execution Options (IFEO) Debugger registry value created for the legitimate process dllhost.exe (ATT&CK ID: T1546.012).
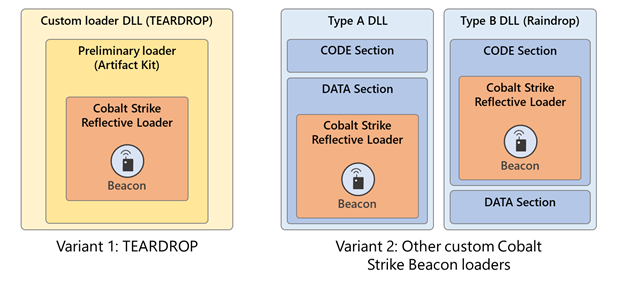
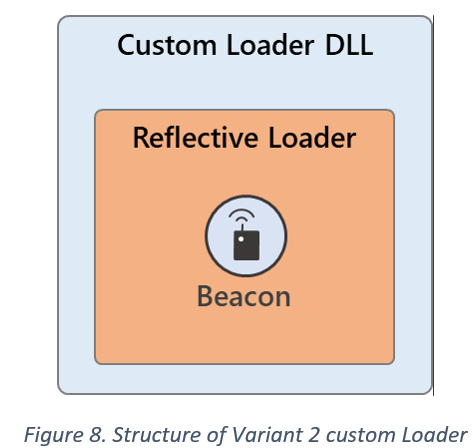
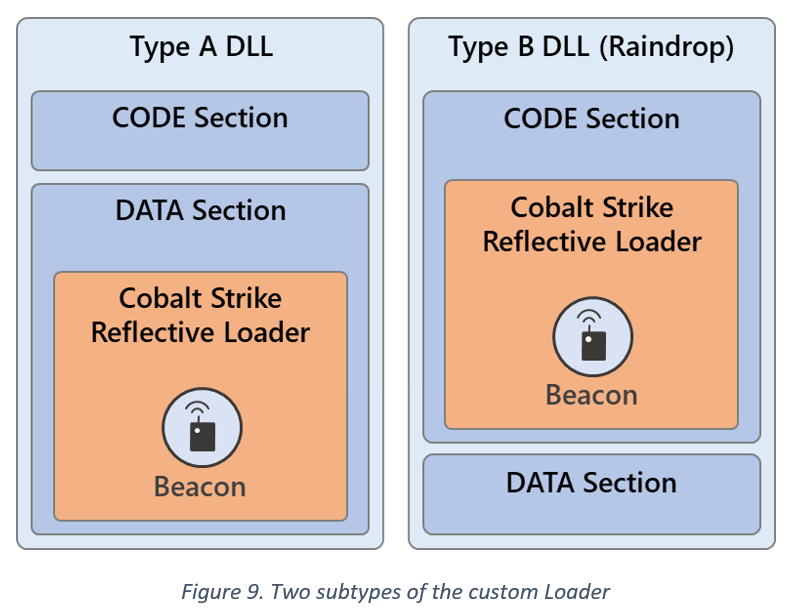
Type A: Decodes/Loads CS's RL from the DLL’s DATA section (detected as Trojan:Win64/Solorigate.SC!dha)
Type B: De-obfuscates/Loads RL from the DLL’s CODE section (aka #Raindrop, detected as Trojan:Win64/Solorigate.SB!dha).
The custom loader DLLs were introduced to compromised systems between the hours of 8:00 AM and 5:00 PM UTC. In one intrusion, the first 2nd stage custom loader (TEARDROP) was introduced to the environment by SolarWinds.BusinessLayerHost.exe at ~ 10:00 AM UTC.
More from Business
Facebook originally a CIA program called "LifeLog".
LifeLog, via DARPA, terminated on Feb 4th, 2004.
Facebook was launched on Feb 4th, 2004.
Many of the LifeLog team became execs at FB.
Zuckerberg is a figurehead.
CIA allowed Cambridge to help Trump win
https://t.co/enzOXDCogV

Pentagon Kills LifeLog
LifeLog, via DARPA, terminated on Feb 4th, 2004.
Facebook was launched on Feb 4th, 2004.
Many of the LifeLog team became execs at FB.
Zuckerberg is a figurehead.
CIA allowed Cambridge to help Trump win
https://t.co/enzOXDCogV

Project: Lifelog
— Robert Horan (@Robby12692) December 13, 2018
Started by DARPA in 1999, the goal of Lifelog was to create a database on civilians without their knowledge, and track everything they do.
The project "ended" on Feb 4th, 2004.
Facebook began the exact same day.
The CIA funneled tens of millions into Facebook. pic.twitter.com/r7hwF0v9kh
Pentagon Kills LifeLog