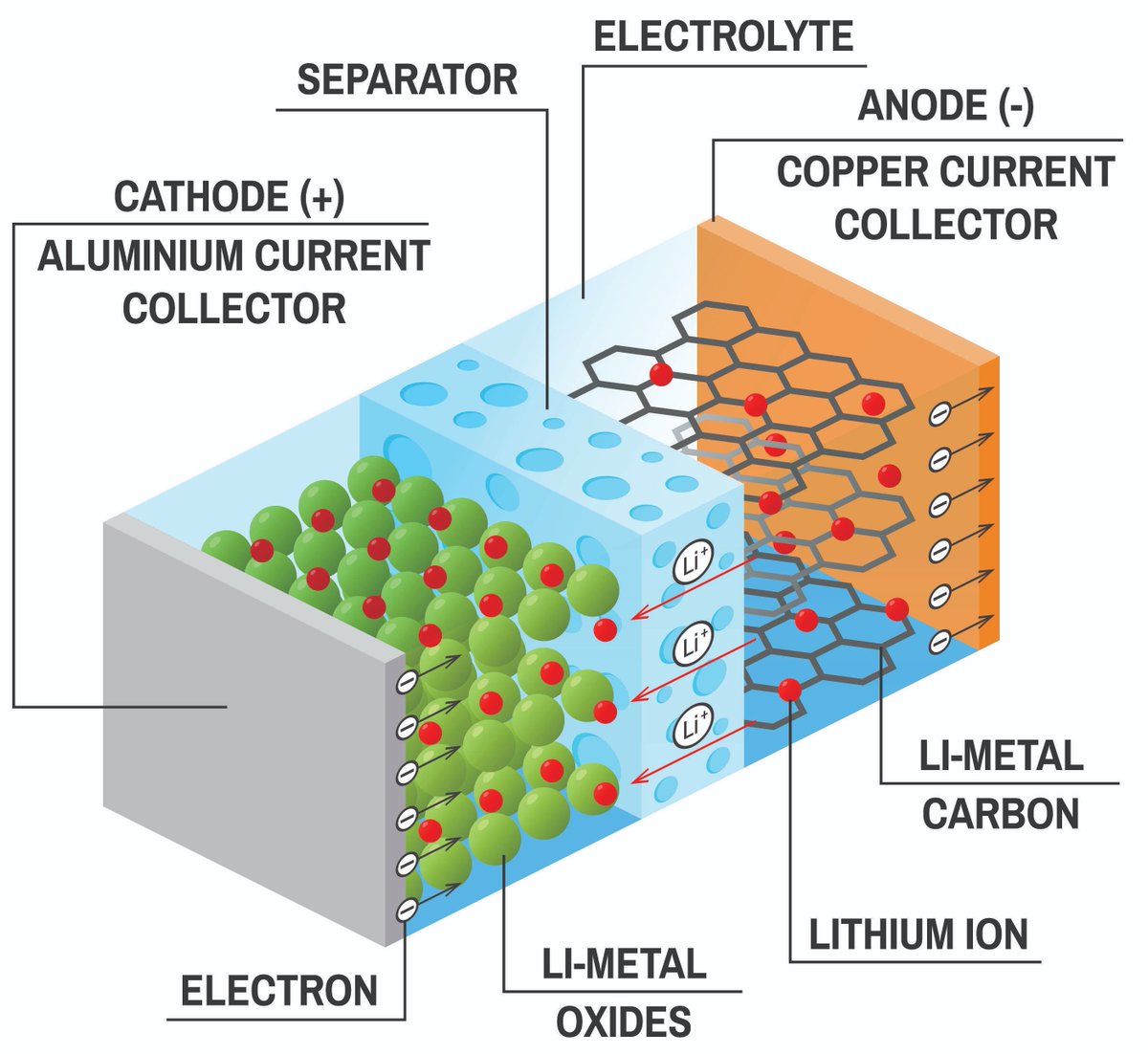
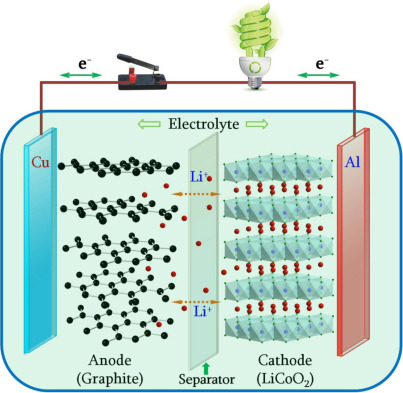
I posted about the Signal messaging application versus Telegram a while ago, and I received a lot of answers about different applications as alternatives. So I'd like to write a thread giving an overview about my perspective on the security of different applications. 1/53
More from Tech
On Wednesday, The New York Times published a blockbuster report on the failures of Facebook’s management team during the past three years. It's.... not flattering, to say the least. Here are six follow-up questions that merit more investigation. 1/
1) During the past year, most of the anger at Facebook has been directed at Mark Zuckerberg. The question now is whether Sheryl Sandberg, the executive charged with solving Facebook’s hardest problems, has caused a few too many of her own. 2/ https://t.co/DTsc3g0hQf
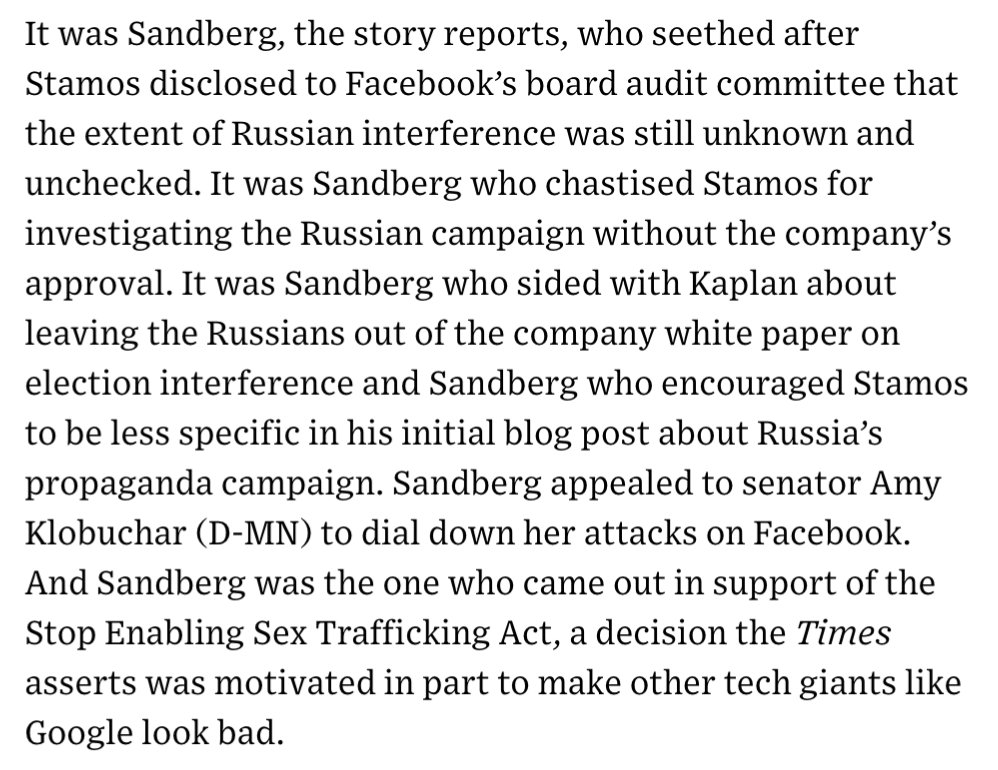
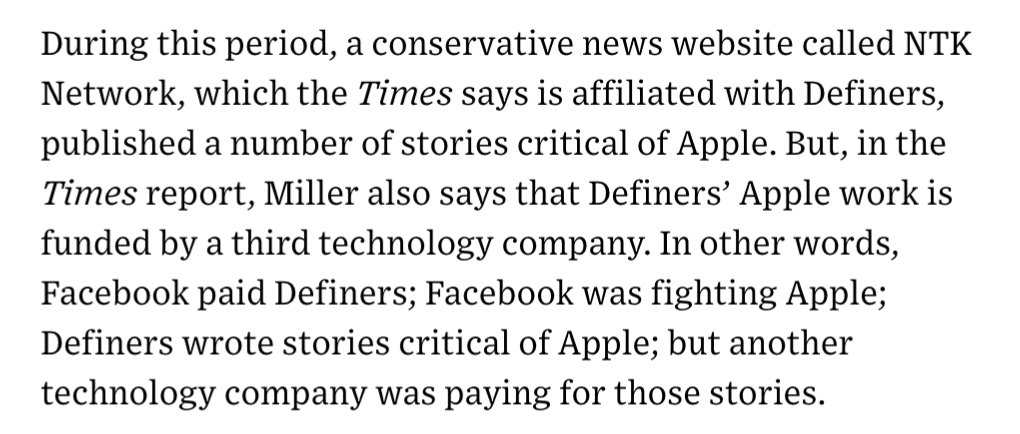
2) One of the juiciest sentences in @nytimes’ piece involves a research group called Definers Public Affairs, which Facebook hired to look into the funding of the company’s opposition. What other tech company was paying Definers to smear Apple? 3/ https://t.co/DTsc3g0hQf
3) The leadership of the Democratic Party has, generally, supported Facebook over the years. But as public opinion turns against the company, prominent Democrats have started to turn, too. What will that relationship look like now? 4/
4) According to the @nytimes, Facebook worked to paint its critics as anti-Semitic, while simultaneously working to spread the idea that George Soros was supporting its critics—a classic tactic of anti-Semitic conspiracy theorists. What exactly were they trying to do there? 5/
1) During the past year, most of the anger at Facebook has been directed at Mark Zuckerberg. The question now is whether Sheryl Sandberg, the executive charged with solving Facebook’s hardest problems, has caused a few too many of her own. 2/ https://t.co/DTsc3g0hQf

2) One of the juiciest sentences in @nytimes’ piece involves a research group called Definers Public Affairs, which Facebook hired to look into the funding of the company’s opposition. What other tech company was paying Definers to smear Apple? 3/ https://t.co/DTsc3g0hQf

3) The leadership of the Democratic Party has, generally, supported Facebook over the years. But as public opinion turns against the company, prominent Democrats have started to turn, too. What will that relationship look like now? 4/
4) According to the @nytimes, Facebook worked to paint its critics as anti-Semitic, while simultaneously working to spread the idea that George Soros was supporting its critics—a classic tactic of anti-Semitic conspiracy theorists. What exactly were they trying to do there? 5/
There has been a lot of discussion about negative emissions technologies (NETs) lately. While we need to be skeptical of assumed planetary-scale engineering and wary of moral hazard, we also need much greater RD&D funding to keep our options open. A quick thread: 1/10
Energy system models love NETs, particularly for very rapid mitigation scenarios like 1.5C (where the alternative is zero global emissions by 2040)! More problematically, they also like tons of NETs in 2C scenarios where NETs are less essential. https://t.co/M3ACyD4cv7 2/10
In model world the math is simple: very rapid mitigation is expensive today, particularly once you get outside the power sector, and technological advancement may make later NETs cheaper than near-term mitigation after a point. 3/10
This is, of course, problematic if the aim is to ensure that particular targets (such as well-below 2C) are met; betting that a "backstop" technology that does not exist today at any meaningful scale will save the day is a hell of a moral hazard. 4/10
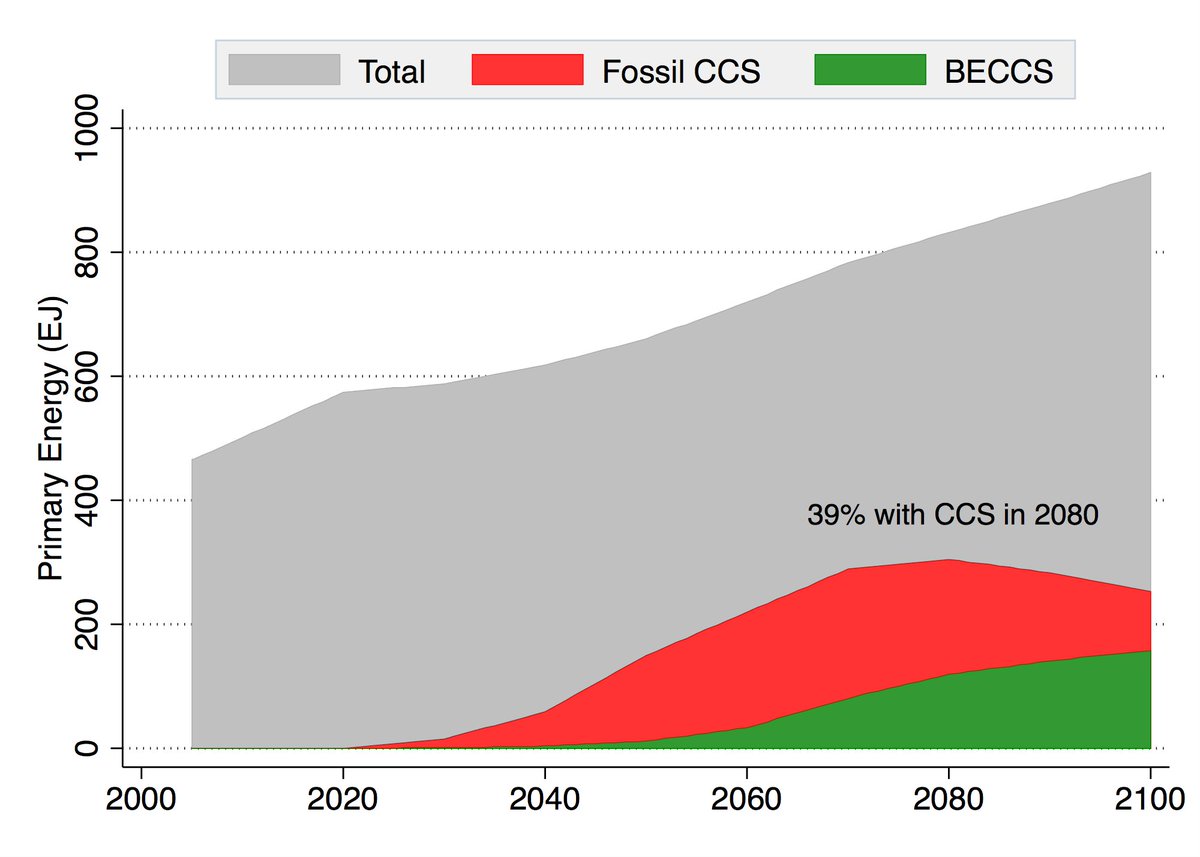
Many models go completely overboard with CCS, seeing a future resurgence of coal and a large part of global primary energy occurring with carbon capture. For example, here is what the MESSAGE SSP2-1.9 scenario shows: 5/10
Energy system models love NETs, particularly for very rapid mitigation scenarios like 1.5C (where the alternative is zero global emissions by 2040)! More problematically, they also like tons of NETs in 2C scenarios where NETs are less essential. https://t.co/M3ACyD4cv7 2/10
There is a lot of confusion about carbon budgets and how quickly emissions need to fall to zero to meet various warming targets. To cut through some of this morass, we can use some very simple emission pathways to explore what various targets would entail. 1/11 pic.twitter.com/Kriedtf0Ec
— Zeke Hausfather (@hausfath) September 24, 2020
In model world the math is simple: very rapid mitigation is expensive today, particularly once you get outside the power sector, and technological advancement may make later NETs cheaper than near-term mitigation after a point. 3/10
This is, of course, problematic if the aim is to ensure that particular targets (such as well-below 2C) are met; betting that a "backstop" technology that does not exist today at any meaningful scale will save the day is a hell of a moral hazard. 4/10
Many models go completely overboard with CCS, seeing a future resurgence of coal and a large part of global primary energy occurring with carbon capture. For example, here is what the MESSAGE SSP2-1.9 scenario shows: 5/10

You May Also Like
✨📱 iOS 12.1 📱✨
🗓 Release date: October 30, 2018
📝 New Emojis: 158
https://t.co/bx8XjhiCiB

New in iOS 12.1: 🥰 Smiling Face With 3 Hearts https://t.co/6eajdvueip

New in iOS 12.1: 🥵 Hot Face https://t.co/jhTv1elltB

New in iOS 12.1: 🥶 Cold Face https://t.co/EIjyl6yZrF

New in iOS 12.1: 🥳 Partying Face https://t.co/p8FDNEQ3LJ

🗓 Release date: October 30, 2018
📝 New Emojis: 158
https://t.co/bx8XjhiCiB

New in iOS 12.1: 🥰 Smiling Face With 3 Hearts https://t.co/6eajdvueip

New in iOS 12.1: 🥵 Hot Face https://t.co/jhTv1elltB

New in iOS 12.1: 🥶 Cold Face https://t.co/EIjyl6yZrF

New in iOS 12.1: 🥳 Partying Face https://t.co/p8FDNEQ3LJ