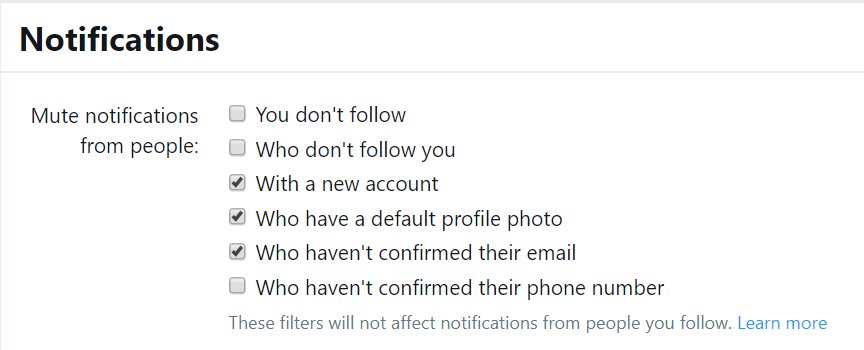
Today I thought to share some Tips that have helped me survive Twitter as a Liberal supporter - in the hopes they'll help you too. A thread:

Go to Settings>Your account>account information (you'll be asked for your password).
Go to Profile, click Edit Profile
More from Internet
There are lots of problems with ad-tech:
* being spied on all the time means that the people of the 21st century are less able to be their authentic selves;
* any data that is collected and retained will eventually breach, creating untold harms;
1/

* data-collection enables for discriminatory business practices ("digital redlining");
* the huge, tangled hairball of adtech companies siphons lots (maybe even most) of the money that should go creators and media orgs; and
2/
* anti-adblock demands browsers and devices that thwart their owners' wishes, a capability that can be exploited for even more nefarious purposes;
That's all terrible, but it's also IRONIC, since it appears that, in addition to everything else, ad-tech is a fraud, a bezzle.
3/
Bezzle was John Kenneth Galbraith's term for "the magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." That is, a rotten log that has yet to be turned over.
4/
Bezzles unwind slowly, then all at once. We've had some important peeks under ad-tech's rotten log, and they're increasing in both intensity and velocity. If you follow @Chronotope, you've had a front-row seat to the
* being spied on all the time means that the people of the 21st century are less able to be their authentic selves;
* any data that is collected and retained will eventually breach, creating untold harms;
1/

* data-collection enables for discriminatory business practices ("digital redlining");
* the huge, tangled hairball of adtech companies siphons lots (maybe even most) of the money that should go creators and media orgs; and
2/
* anti-adblock demands browsers and devices that thwart their owners' wishes, a capability that can be exploited for even more nefarious purposes;
That's all terrible, but it's also IRONIC, since it appears that, in addition to everything else, ad-tech is a fraud, a bezzle.
3/
Bezzle was John Kenneth Galbraith's term for "the magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." That is, a rotten log that has yet to be turned over.
4/
Bezzles unwind slowly, then all at once. We've had some important peeks under ad-tech's rotten log, and they're increasing in both intensity and velocity. If you follow @Chronotope, you've had a front-row seat to the
The numbers are all fking fake, the metrics are bullshit, the agencies responsible for enforcing good practices are knowing bullshiters enforcing and profiting off all the fake numbers and none of the models make sense at scale of actual human users. https://t.co/sfmdrxGBNJ pic.twitter.com/thvicDEL29
— Aram Zucker-Scharff (@Chronotope) December 26, 2018
The Internet and mobile phones have taken over our lives. But it comes with increasing security concerns. Website data breaches, phishing attacks, and other online scams are commonplace. Here's a thread for regular people on how to increase your security online.
#StaySafeOnline
#1
Go to your Google account settings. Revoke permissions from all the apps you don't use: https://t.co/cMGgSgtRTI
Also check if any app has access to your contacts or - gasp! - your entire email. Strongly reconsider both, especially access to your email.
Giving access to your contacts lets companies spam those people.
Giving access to your email - email organising apps, for instance - renders your online security meaningless. Password resets are often done with email, and if an external entity can access that, game over!
#2
Go to your Twitter account settings and revoke permissions from all the apps you don't use or trust:
https://t.co/lXxCgdnaXH
Online quizzes and such sites often ask for permission to post tweets for you, read your tweets, and even your DMs!.
People click "OK" without reading the fine print.
But imagine the security and privacy risk with having some unknown entity be able to post tweets and read your private DMs just to post the results of what Game of Thrones character you are.
#StaySafeOnline
#1
Go to your Google account settings. Revoke permissions from all the apps you don't use: https://t.co/cMGgSgtRTI
Also check if any app has access to your contacts or - gasp! - your entire email. Strongly reconsider both, especially access to your email.
Giving access to your contacts lets companies spam those people.
Giving access to your email - email organising apps, for instance - renders your online security meaningless. Password resets are often done with email, and if an external entity can access that, game over!
#2
Go to your Twitter account settings and revoke permissions from all the apps you don't use or trust:
https://t.co/lXxCgdnaXH
Online quizzes and such sites often ask for permission to post tweets for you, read your tweets, and even your DMs!.
People click "OK" without reading the fine print.
But imagine the security and privacy risk with having some unknown entity be able to post tweets and read your private DMs just to post the results of what Game of Thrones character you are.
You May Also Like
"I really want to break into Product Management"
make products.
"If only someone would tell me how I can get a startup to notice me."
Make Products.
"I guess it's impossible and I'll never break into the industry."
MAKE PRODUCTS.
Courtesy of @edbrisson's wonderful thread on breaking into comics – https://t.co/TgNblNSCBj – here is why the same applies to Product Management, too.
There is no better way of learning the craft of product, or proving your potential to employers, than just doing it.
You do not need anybody's permission. We don't have diplomas, nor doctorates. We can barely agree on a single standard of what a Product Manager is supposed to do.
But – there is at least one blindingly obvious industry consensus – a Product Manager makes Products.
And they don't need to be kept at the exact right temperature, given endless resource, or carefully protected in order to do this.
They find their own way.
make products.
"If only someone would tell me how I can get a startup to notice me."
Make Products.
"I guess it's impossible and I'll never break into the industry."
MAKE PRODUCTS.
Courtesy of @edbrisson's wonderful thread on breaking into comics – https://t.co/TgNblNSCBj – here is why the same applies to Product Management, too.
"I really want to break into comics"
— Ed Brisson (@edbrisson) December 4, 2018
make comics.
"If only someone would tell me how I can get an editor to notice me."
Make Comics.
"I guess it's impossible and I'll never break into the industry."
MAKE COMICS.
There is no better way of learning the craft of product, or proving your potential to employers, than just doing it.
You do not need anybody's permission. We don't have diplomas, nor doctorates. We can barely agree on a single standard of what a Product Manager is supposed to do.
But – there is at least one blindingly obvious industry consensus – a Product Manager makes Products.
And they don't need to be kept at the exact right temperature, given endless resource, or carefully protected in order to do this.
They find their own way.