This is some true bullshit. A fully radicalized white man methodically builds and detonates a bomb like he saw in Speed complete with creepy music and a fresh, highly obvious target.
More from Crime
THREAD PART 1.
On Sunday 21st June, 14 year old Noah Donohoe left his home to meet his friends at Cave Hill Belfast to study for school. #RememberMyNoah💙

He was on his black Apollo mountain bike, fully dressed, wearing a helmet and carrying a backpack containing his laptop and 2 books with his name on them. He also had his mobile phone with him.
On the 27th of June. Noah's naked body was sadly discovered 950m inside a storm drain, between access points. This storm drain was accessible through an area completely unfamiliar to him, behind houses at Northwood Road. https://t.co/bpz3Rmc0wq
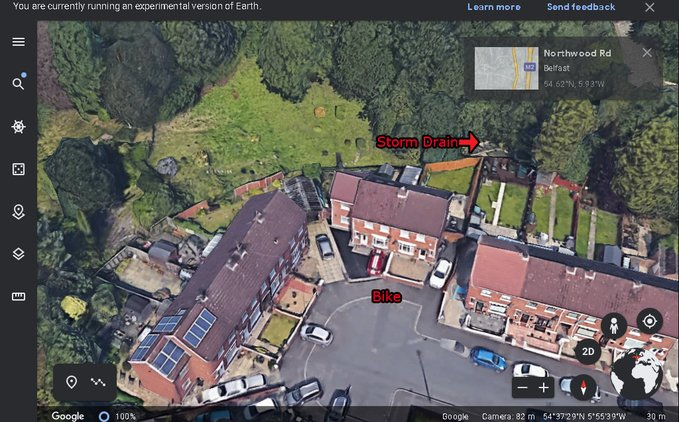
"Noah's body was found by specially trained police officers between two drain access points within a section of the tunnel running under the Translink access road," said Mr McCrisken."
Noah's bike was also found near a house, behind a car, in the same area. It had been there for more than 24 hours before a member of public who lived in the street said she read reports of a missing child and checked the bike and phoned the police.
On Sunday 21st June, 14 year old Noah Donohoe left his home to meet his friends at Cave Hill Belfast to study for school. #RememberMyNoah💙

He was on his black Apollo mountain bike, fully dressed, wearing a helmet and carrying a backpack containing his laptop and 2 books with his name on them. He also had his mobile phone with him.
On the 27th of June. Noah's naked body was sadly discovered 950m inside a storm drain, between access points. This storm drain was accessible through an area completely unfamiliar to him, behind houses at Northwood Road. https://t.co/bpz3Rmc0wq

"Noah's body was found by specially trained police officers between two drain access points within a section of the tunnel running under the Translink access road," said Mr McCrisken."
Noah's bike was also found near a house, behind a car, in the same area. It had been there for more than 24 hours before a member of public who lived in the street said she read reports of a missing child and checked the bike and phoned the police.
Between this guy and the Nashville bomber, I guess it's time to
*sigh*
talk about "lizard people," David Ickes, QAnon, and the extreme antisemitism lurking like a rabid Loch Ness monster in this soup of conspiracy.
*sigh*
talk about "lizard people," David Ickes, QAnon, and the extreme antisemitism lurking like a rabid Loch Ness monster in this soup of conspiracy.
Trumpist lawyer Lin Wood, who I believe has petitions pending before the Supreme Court, is in the middle of a flurry of tweets alleging Chief Justice John Roberts murdered a child on video. Also something about a Lizard Squad and assassins and, well, lots of stuff. pic.twitter.com/EPbeQLyDIk
— Helen Kennedy (@HelenKennedy) January 4, 2021
My students @maxzks and Tushar Jois spent most of the summer going through every piece of public documentation, forensics report, and legal document we could find to figure out how police were “breaking phone encryption”. 1/
This was prompted by a claim from someone knowledgeable, who claimed that forensics companies no longer had the ability to break the Apple Secure Enclave Processor, which would make it very hard to crack the password of a locked, recent iPhone. 2/
We wrote an enormous report about what we found, which we’ll release after the holidays. The TL;DR is kind of depressing:
Authorities don’t need to break phone encryption in most cases, because modern phone encryption sort of sucks. 3/
I’ll focus on Apple here but Android is very similar. The top-level is that, to break encryption on an Apple phone you need to get the encryption keys. Since these are derived from the user’s passcode, you either need to guess that — or you need the user to have entered it. 4/
Guessing the password is hard on recent iPhones because there’s (at most) a 10-guess limit enforced by the Secure Enclave Processor (SEP). There’s good evidence that at one point in 2018 a company called GrayKey had a SEP exploit that did this for the X. See photo. 5/

ACLU is suing the FBI over its efforts to break into encrypted devices. https://t.co/TN8X0Slmnf
— Zack Whittaker (@zackwhittaker) December 22, 2020
This was prompted by a claim from someone knowledgeable, who claimed that forensics companies no longer had the ability to break the Apple Secure Enclave Processor, which would make it very hard to crack the password of a locked, recent iPhone. 2/
We wrote an enormous report about what we found, which we’ll release after the holidays. The TL;DR is kind of depressing:
Authorities don’t need to break phone encryption in most cases, because modern phone encryption sort of sucks. 3/
I’ll focus on Apple here but Android is very similar. The top-level is that, to break encryption on an Apple phone you need to get the encryption keys. Since these are derived from the user’s passcode, you either need to guess that — or you need the user to have entered it. 4/
Guessing the password is hard on recent iPhones because there’s (at most) a 10-guess limit enforced by the Secure Enclave Processor (SEP). There’s good evidence that at one point in 2018 a company called GrayKey had a SEP exploit that did this for the X. See photo. 5/






















