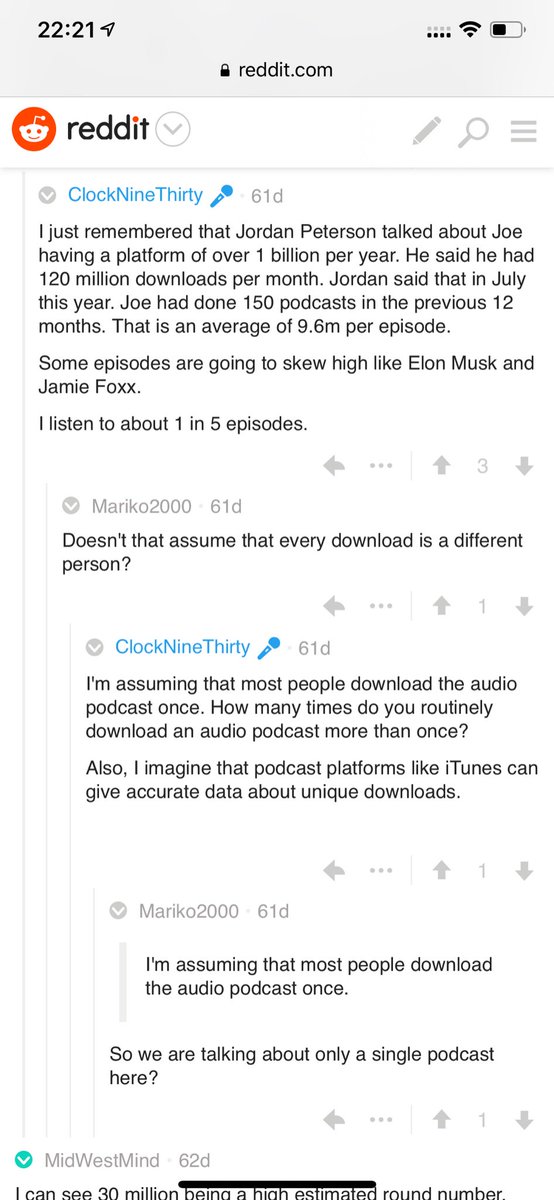
She is informing her audience on what needs to be done to the US Capitol!
What is captured next is alarming & deadly?
2/?
@texasgop @tedcruz @KenPaxtonTX #txlege
\u201cWe\u2019re going to be breaking those windows\u201d pic.twitter.com/8PGMxEBktU
— Dr Mike Galsworthy (@mikegalsworthy) January 9, 2021
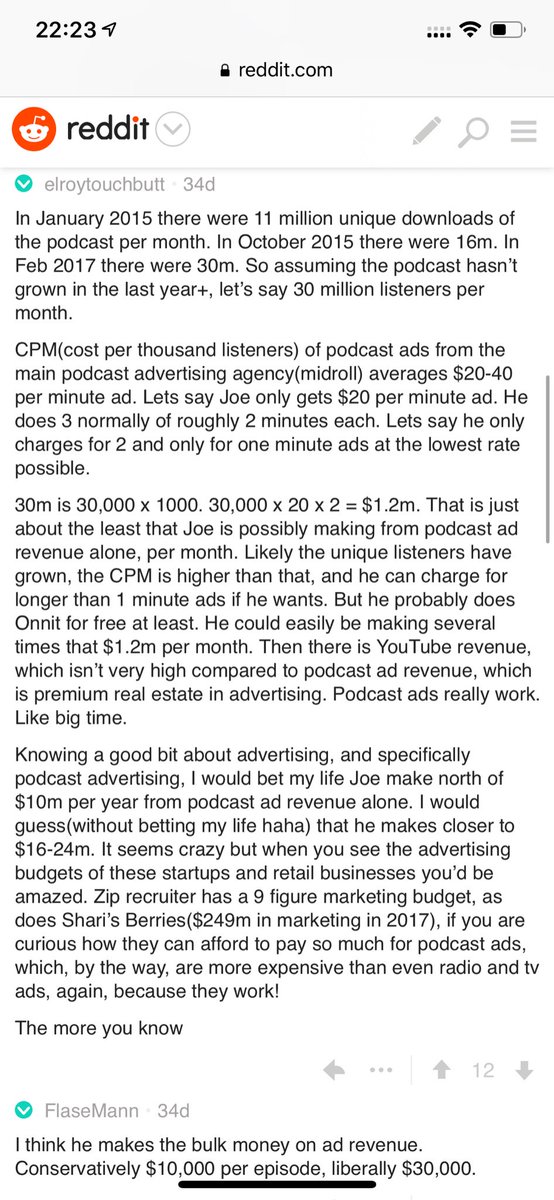
The 13 people murdered by Trump's death row killing spree:
— Cori Bush (@CoriBush) January 17, 2021
Daniel Lee
Wesley Purkey
Dustin Honken
Lezmond Mitchell
Keith Nelson
William LeCroy Jr.
Christopher Vialva
Orlando Hall
Brandon Bernard
Alfred Bourgeois
Lisa Montgomery
Corey Johnson
Dustin Higgs
Say their names.