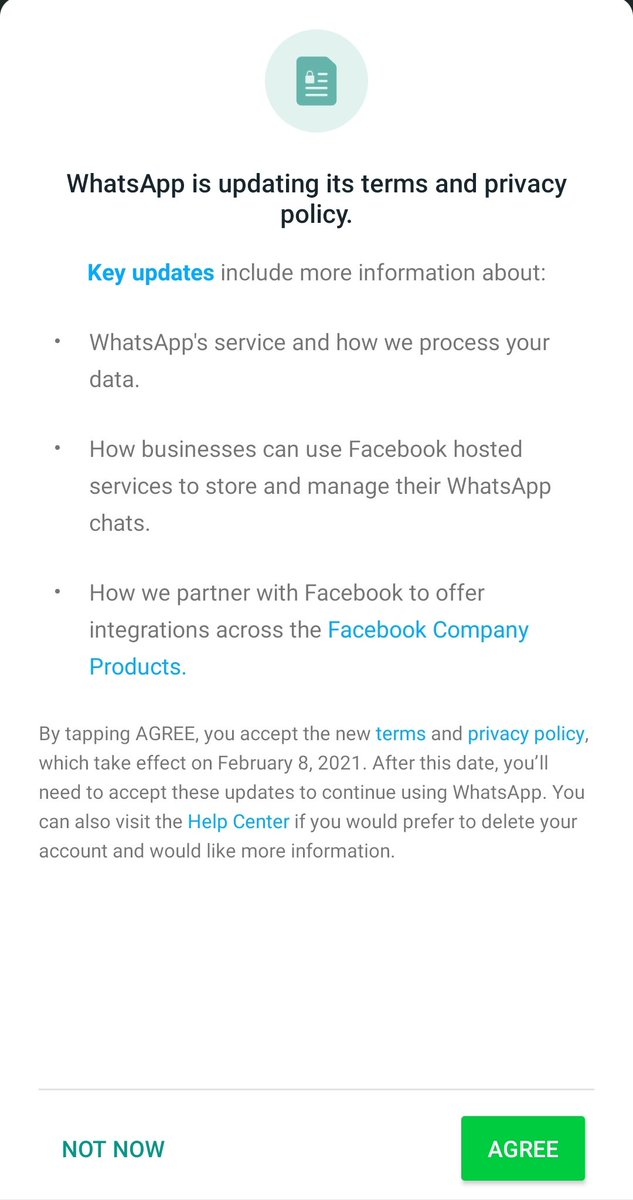
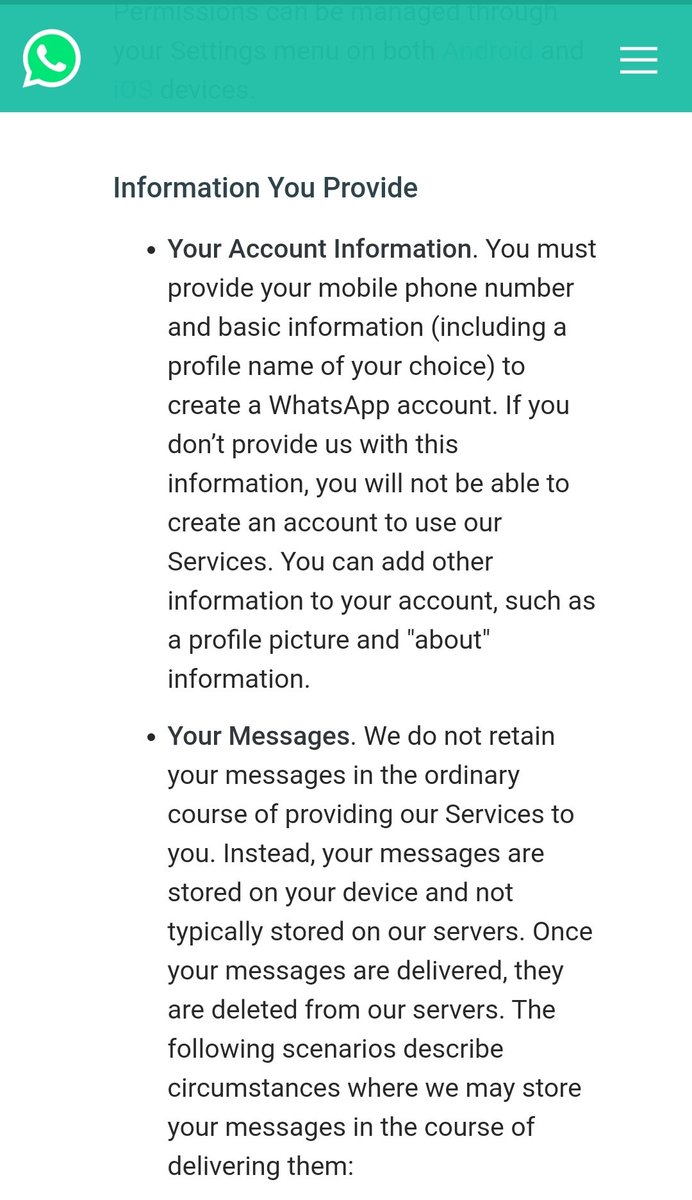
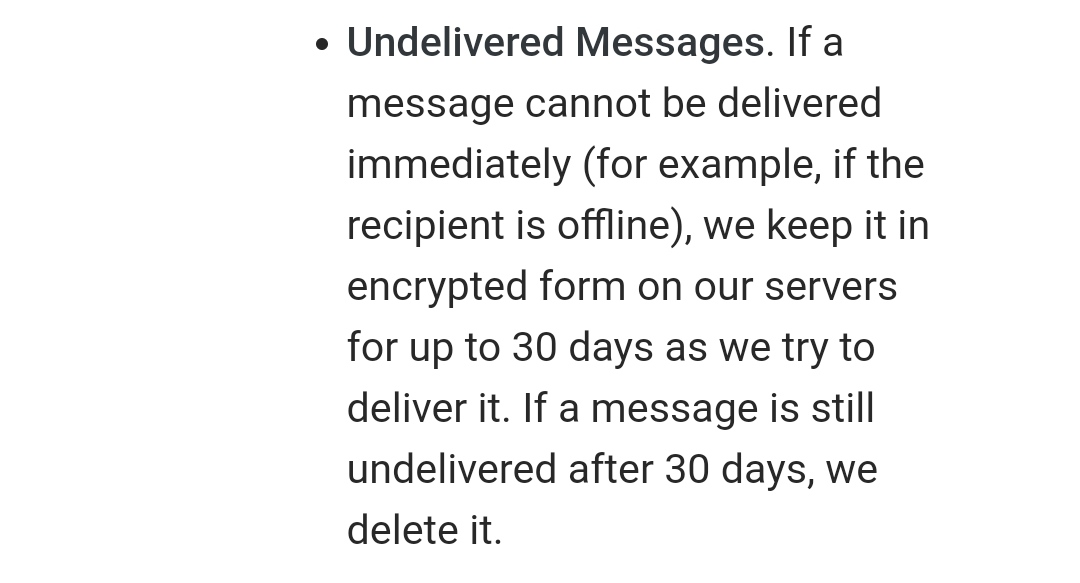
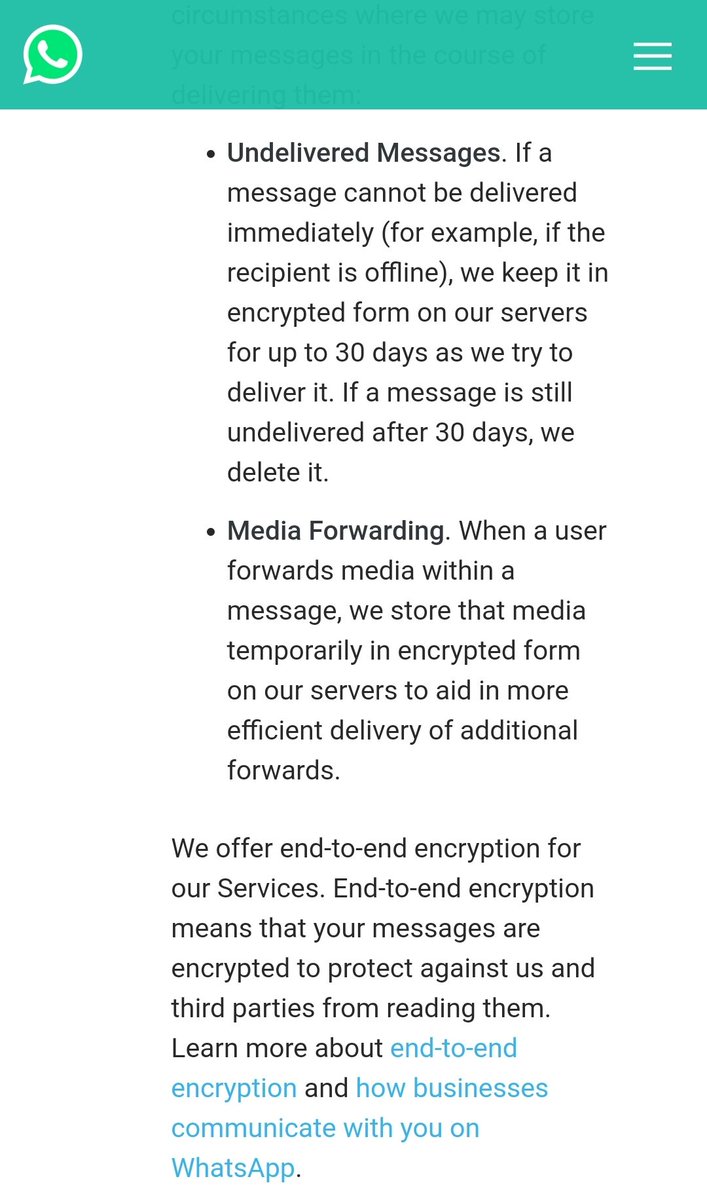
Accounts are closed! Why? Because YOU DEPEND ON A CENTRAL SERVER. And you don't OWN the server! Don't depend on adversary weapons! Claim your digital weapons in the info-war >> https://t.co/TBTjRB93pO - FULL THREAD 🔻🔻






@Are_you_aware_ @TBG9270584 @Retuz2 @YorkieWR @lizzywales @Anontruther911 @julijaceh @lizzywales @PrismPrime @kolat_ca @magicNmoonbeams @Urylle @5Agenda21 @fismaex @HegKong @gabrieltoma @mslove_TLB @melaniariz @blue_augustus
More from Internet
SolarWinds follow up. Very good tweet explaining what happened.
Basically what this means is that SolarWinds itself was exploited. Someone posted an infected update as legitimate (digitally signed), leading customers to download a bad update.
“Multiple trojanized updates were digitally signed from March - May 2020 and posted to the SolarWinds updates website” https://t.co/8e3bMFWXYu

FireEye then explains that infected organizations were approached and exploited. This is a separate Step 2.
At this point, information is already going to “malicious domains” without extra intervention, after the malware does nothing for “up to two weeks”

Hackers reportedly slipped malware into prior SolarWinds software updates, which gave them access to a "God-mode" for infected networks, including the Treasury and Commerce departments.
— Wes Wilson (@weswilson4) December 14, 2020
The Pentagon is also a SolarWinds customer.https://t.co/Srcoztssol https://t.co/OgMhAjJqPx
Basically what this means is that SolarWinds itself was exploited. Someone posted an infected update as legitimate (digitally signed), leading customers to download a bad update.
“Multiple trojanized updates were digitally signed from March - May 2020 and posted to the SolarWinds updates website” https://t.co/8e3bMFWXYu

FireEye then explains that infected organizations were approached and exploited. This is a separate Step 2.
At this point, information is already going to “malicious domains” without extra intervention, after the malware does nothing for “up to two weeks”

You May Also Like
Recently, the @CNIL issued a decision regarding the GDPR compliance of an unknown French adtech company named "Vectaury". It may seem like small fry, but the decision has potential wide-ranging impacts for Google, the IAB framework, and today's adtech. It's thread time! 👇
It's all in French, but if you're up for it you can read:
• Their blog post (lacks the most interesting details): https://t.co/PHkDcOT1hy
• Their high-level legal decision: https://t.co/hwpiEvjodt
• The full notification: https://t.co/QQB7rfynha
I've read it so you needn't!
Vectaury was collecting geolocation data in order to create profiles (eg. people who often go to this or that type of shop) so as to power ad targeting. They operate through embedded SDKs and ad bidding, making them invisible to users.
The @CNIL notes that profiling based off of geolocation presents particular risks since it reveals people's movements and habits. As risky, the processing requires consent — this will be the heart of their assessment.
Interesting point: they justify the decision in part because of how many people COULD be targeted in this way (rather than how many have — though they note that too). Because it's on a phone, and many have phones, it is considered large-scale processing no matter what.
It's all in French, but if you're up for it you can read:
• Their blog post (lacks the most interesting details): https://t.co/PHkDcOT1hy
• Their high-level legal decision: https://t.co/hwpiEvjodt
• The full notification: https://t.co/QQB7rfynha
I've read it so you needn't!
Vectaury was collecting geolocation data in order to create profiles (eg. people who often go to this or that type of shop) so as to power ad targeting. They operate through embedded SDKs and ad bidding, making them invisible to users.
The @CNIL notes that profiling based off of geolocation presents particular risks since it reveals people's movements and habits. As risky, the processing requires consent — this will be the heart of their assessment.
Interesting point: they justify the decision in part because of how many people COULD be targeted in this way (rather than how many have — though they note that too). Because it's on a phone, and many have phones, it is considered large-scale processing no matter what.