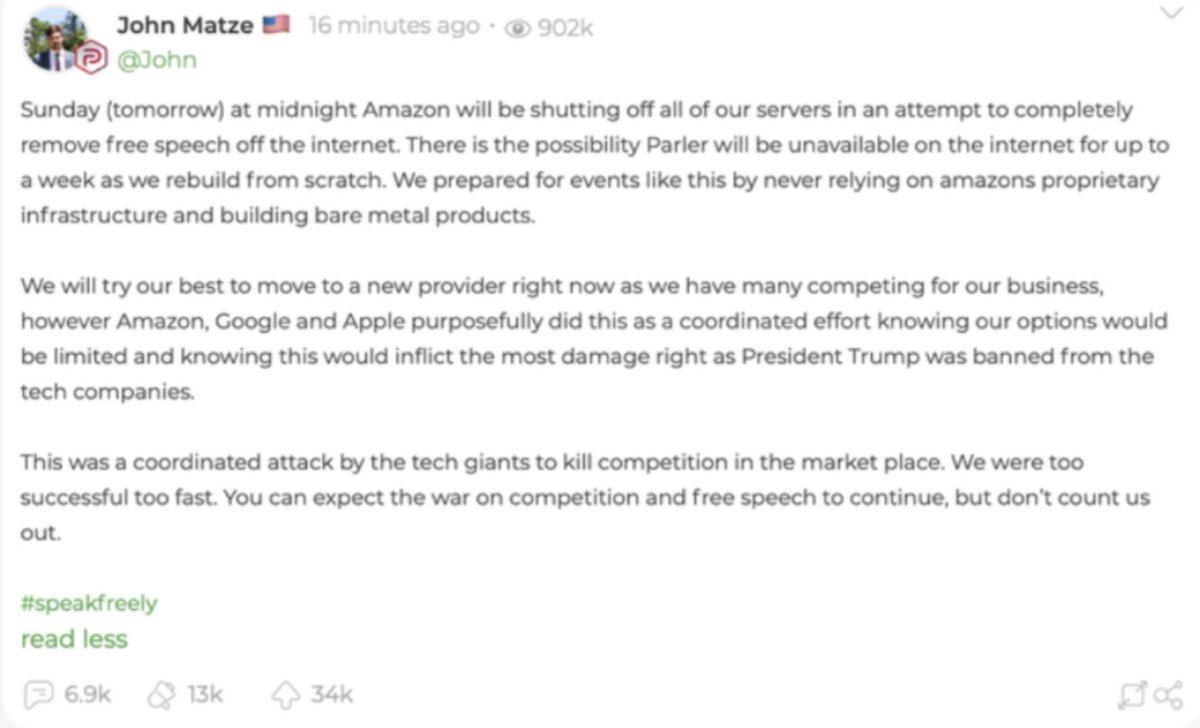
Categories Internet
7 days
30 days
All time
Recent
Popular
Or, you could let us know when you figure out why it was trending yesterday and the users are complaining which is why Vice wrote about it. Why I'm saying what I am.
There's an assumption here that this problem is fixed bc it was already hacked.
It's not.
We have ppl freezing and dying in TX right now because some ppl who thought they were really smart never spoke to anyone with actual experience with energy systems in extreme cold climates.
Texans are waiting for a solution to a preventable problem.
Farmers are saying that now, not during a crisis, they have to wait for a JD tech to arrive to help them.
The assumption that bc SOME farmers said screw this and used hacked firmware to get around that obstacle doesn't mean that all farmers are doing that.
If all farmers were using hacked firmware we wouldn't be discussing this right now would we?
Of course no one has pointed out that another issue here is that no one at John Deere has figured out they don't have enough staff to quickly and reliably SOLVE problems.
The locked firmware is just one of many issues here.
By not giving people a fast solution they're causing this and other issues.
So what I'm saying is somebody at John Deere needs to examine all of this.
There's an assumption here that this problem is fixed bc it was already hacked.
It's not.
Let us know when you've found the supply chain hack that's already there
— SleeplessOrphan (@sleeplessorphan) February 20, 2021
We have ppl freezing and dying in TX right now because some ppl who thought they were really smart never spoke to anyone with actual experience with energy systems in extreme cold climates.
Texans are waiting for a solution to a preventable problem.
Farmers are saying that now, not during a crisis, they have to wait for a JD tech to arrive to help them.
The assumption that bc SOME farmers said screw this and used hacked firmware to get around that obstacle doesn't mean that all farmers are doing that.
If all farmers were using hacked firmware we wouldn't be discussing this right now would we?
Of course no one has pointed out that another issue here is that no one at John Deere has figured out they don't have enough staff to quickly and reliably SOLVE problems.
The locked firmware is just one of many issues here.
By not giving people a fast solution they're causing this and other issues.
So what I'm saying is somebody at John Deere needs to examine all of this.
We’ve spent the last ten months building #CitizenBrowser, a project that aims to peek inside the Black Box of social media algorithms, by building a nationwide panel to share data with us. Today, we are publishing our first story from the project. /1
.@corintxt crunched the numbers and found that after Facebook flipped the switch for political ads, partisan content elbowed out reputable news outlets in our panelists’ news feeds. https://t.co/Z0kibSBeQZ /2
You can learn more in our methodology, where we describe how we did this and what steps we took to ensure that we preserved the panelists' privacy. https://t.co/UYbTXAjy5i /3
Personally, this project is the culmination of years of experiments trying to figure out how to collect data from social media platforms in a way that can lead to meaningful reporting. I’ve described a couple of highlights below 👇 /4
My first attempt was in 2016 at Propublica, when I was working with @JuliaAngwin . We were interested in seeing if there was a difference in the Ad interests FB disclosed to users in their settings and the interests they showed to marketers. /5
.@corintxt crunched the numbers and found that after Facebook flipped the switch for political ads, partisan content elbowed out reputable news outlets in our panelists’ news feeds. https://t.co/Z0kibSBeQZ /2
You can learn more in our methodology, where we describe how we did this and what steps we took to ensure that we preserved the panelists' privacy. https://t.co/UYbTXAjy5i /3
Personally, this project is the culmination of years of experiments trying to figure out how to collect data from social media platforms in a way that can lead to meaningful reporting. I’ve described a couple of highlights below 👇 /4
My first attempt was in 2016 at Propublica, when I was working with @JuliaAngwin . We were interested in seeing if there was a difference in the Ad interests FB disclosed to users in their settings and the interests they showed to marketers. /5
🚨 🦮 Seven ways to test for accessibility using only what is already in browser developer tools of Chromium browsers https://t.co/C7kdbigHGE
@MSEdgeDev @EdgeDevTools @ChromiumDev
#tools #accessibility #browsers
Also, a thread: 👇🏼
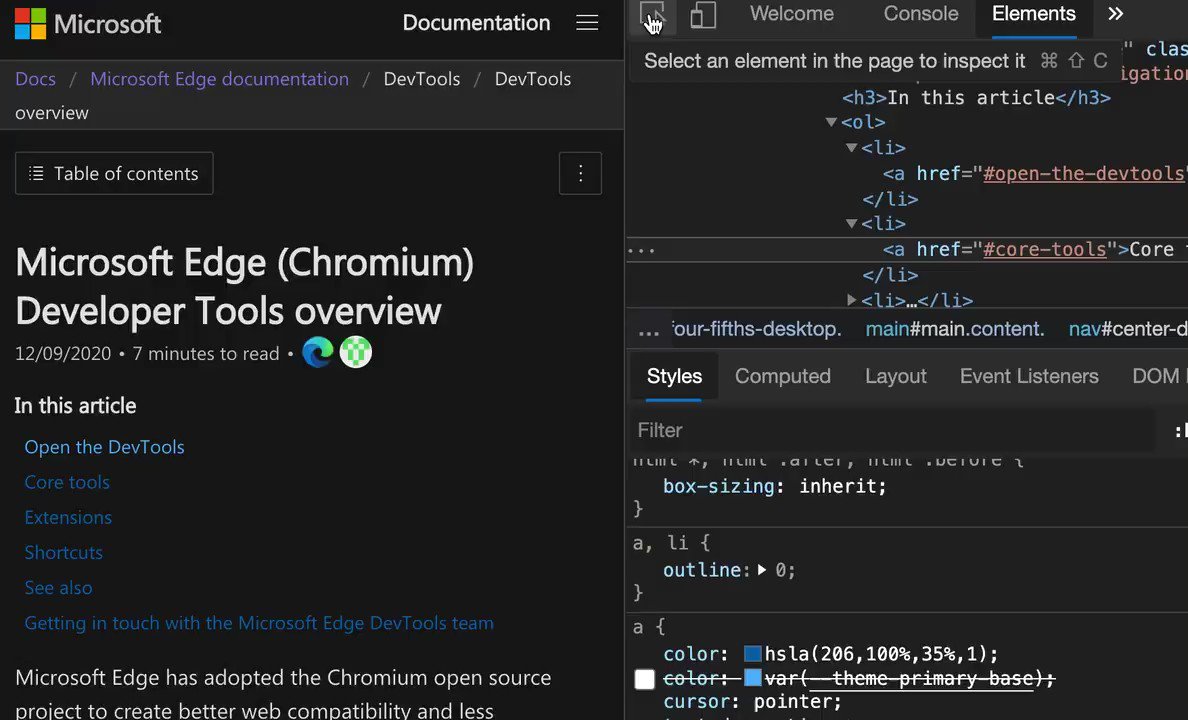
Issues pane, powered by @webhintio, listing accessibility issues with explanations why these are problems, links to more info and direct links to the tools where to fix the problem. https://t.co/4K5RynHhbg
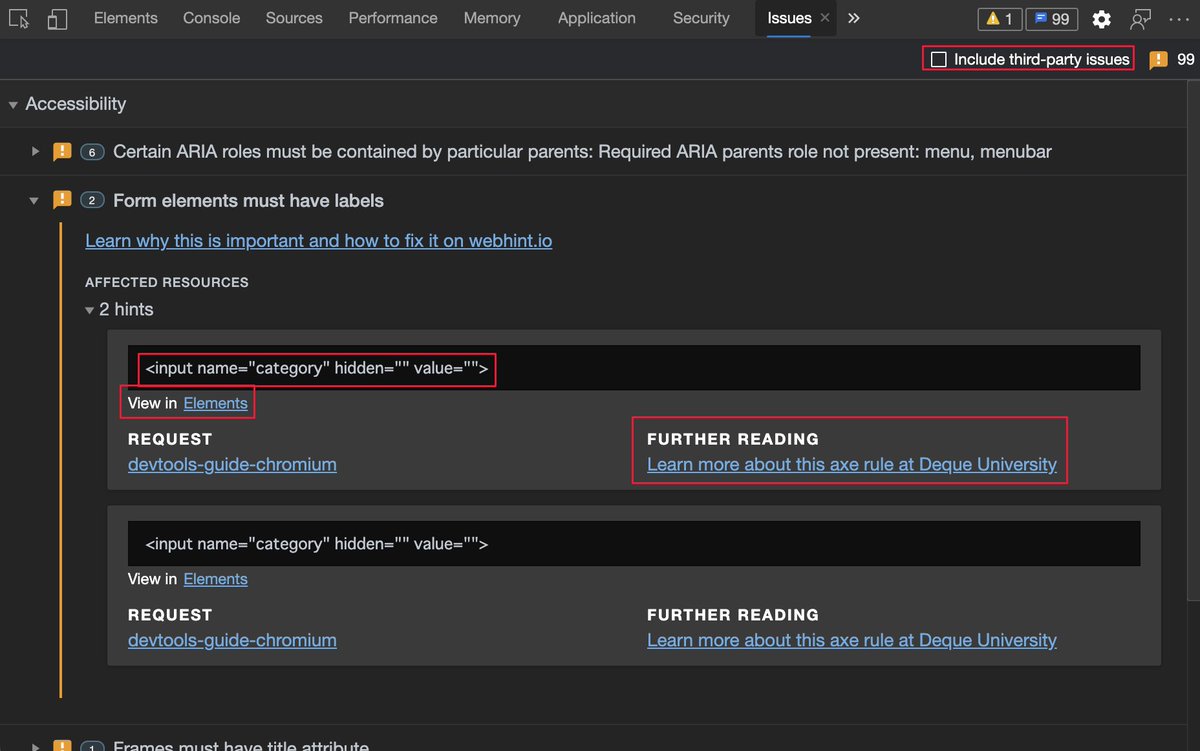
The inspect element overlay showing accessibility relevant information of the element, including contrast information, ARIA name, role and if it can be focused via keyboard.
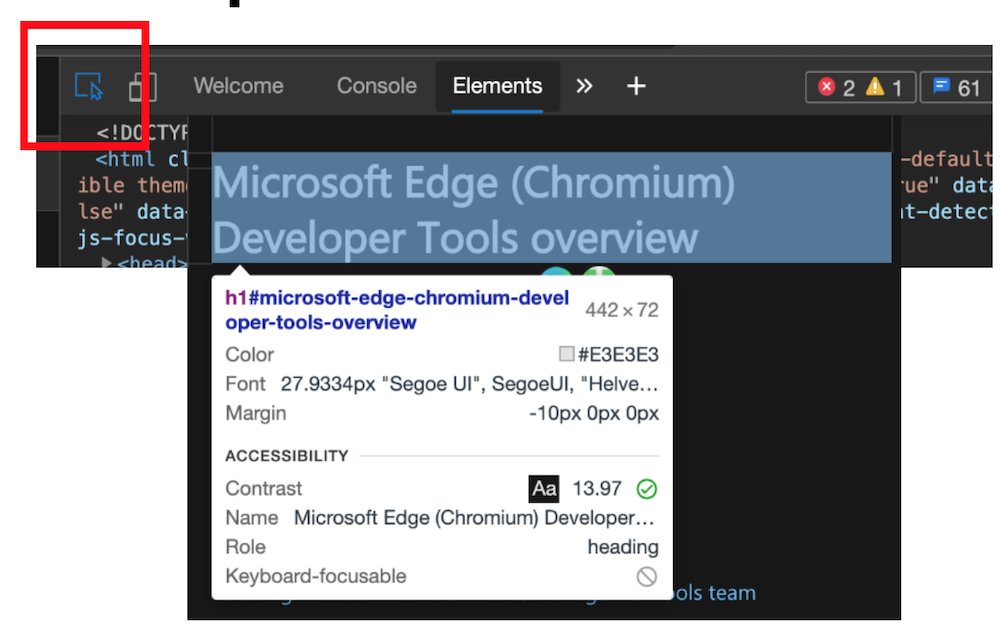
Colour picker with contrast information offering colours that are AA/AAA compliant. You can also see compliant colours indicated by a line on the colour patch.
Note: the current algorithm fails to take font weight into consideration, that's why there will be a new one.

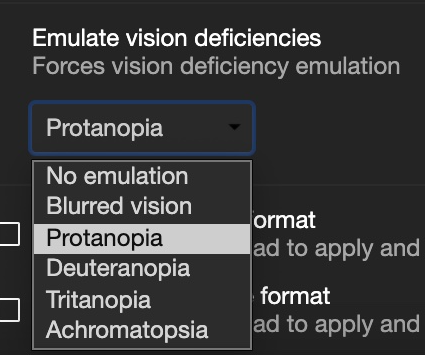
Vision deficit ("colour blindness") emulation. You can see what your product looks like for different visitors.
https://t.co/bxj1vySCAb
@MSEdgeDev @EdgeDevTools @ChromiumDev
#tools #accessibility #browsers
Also, a thread: 👇🏼

Issues pane, powered by @webhintio, listing accessibility issues with explanations why these are problems, links to more info and direct links to the tools where to fix the problem. https://t.co/4K5RynHhbg

The inspect element overlay showing accessibility relevant information of the element, including contrast information, ARIA name, role and if it can be focused via keyboard.

Colour picker with contrast information offering colours that are AA/AAA compliant. You can also see compliant colours indicated by a line on the colour patch.
Note: the current algorithm fails to take font weight into consideration, that's why there will be a new one.

Vision deficit ("colour blindness") emulation. You can see what your product looks like for different visitors.
https://t.co/bxj1vySCAb

Well, this should be a depressing read -- notably because the UK and the US are both terrible when it comes to data protection, but the UK appears to be getting a pass. So much for 'adequacy'.
A few initial thoughts on the Draft Decision on UK Adequacy: https://t.co/ncAqc93UFm
The decision goes into great detail about the state of the UK surveillance system, and notably, "bulk acquisition" of data, and I think I get their argument. /1
For one, while the UK allows similar "bulk powers," it differs from the US regime both in terms of proportionality, oversight, and even notice. Some of this came about after the Privacy International case in 2019 (Privacy International) v Investigatory
Powers Tribunal [2019]) /2
Whereas, other bits were already baked in by virtue of the fact that the Human Rights Act is a thing (This concept doesn't exist in the US; rather we hand-wave about the Constitution and Bill of Rights, and then selectively apply it) /3
For example, UK bulk surveillance (I'm keeping this broad, but the draft policy breaksk it down), substantially limits collection to three agencies: MI5, MI6, and GHCQ). By contrast, it's a bit of a free-for-all in the US, where varying policies /4
At least we have a draft of the adequacy decision. I haven't read it yet, mostly because I'm afraid I'll be disappointed that it doesn't address the UK's penchant for surveillance. https://t.co/puJiVET2SJ
— Don Edwards (@DMEdwards) February 20, 2021
A few initial thoughts on the Draft Decision on UK Adequacy: https://t.co/ncAqc93UFm
The decision goes into great detail about the state of the UK surveillance system, and notably, "bulk acquisition" of data, and I think I get their argument. /1
For one, while the UK allows similar "bulk powers," it differs from the US regime both in terms of proportionality, oversight, and even notice. Some of this came about after the Privacy International case in 2019 (Privacy International) v Investigatory
Powers Tribunal [2019]) /2
Whereas, other bits were already baked in by virtue of the fact that the Human Rights Act is a thing (This concept doesn't exist in the US; rather we hand-wave about the Constitution and Bill of Rights, and then selectively apply it) /3
For example, UK bulk surveillance (I'm keeping this broad, but the draft policy breaksk it down), substantially limits collection to three agencies: MI5, MI6, and GHCQ). By contrast, it's a bit of a free-for-all in the US, where varying policies /4
The Internet and mobile phones have taken over our lives. But it comes with increasing security concerns. Website data breaches, phishing attacks, and other online scams are commonplace. Here's a thread for regular people on how to increase your security online.
#StaySafeOnline
#1
Go to your Google account settings. Revoke permissions from all the apps you don't use: https://t.co/cMGgSgtRTI
Also check if any app has access to your contacts or - gasp! - your entire email. Strongly reconsider both, especially access to your email.
Giving access to your contacts lets companies spam those people.
Giving access to your email - email organising apps, for instance - renders your online security meaningless. Password resets are often done with email, and if an external entity can access that, game over!
#2
Go to your Twitter account settings and revoke permissions from all the apps you don't use or trust:
https://t.co/lXxCgdnaXH
Online quizzes and such sites often ask for permission to post tweets for you, read your tweets, and even your DMs!.
People click "OK" without reading the fine print.
But imagine the security and privacy risk with having some unknown entity be able to post tweets and read your private DMs just to post the results of what Game of Thrones character you are.
#StaySafeOnline
#1
Go to your Google account settings. Revoke permissions from all the apps you don't use: https://t.co/cMGgSgtRTI
Also check if any app has access to your contacts or - gasp! - your entire email. Strongly reconsider both, especially access to your email.
Giving access to your contacts lets companies spam those people.
Giving access to your email - email organising apps, for instance - renders your online security meaningless. Password resets are often done with email, and if an external entity can access that, game over!
#2
Go to your Twitter account settings and revoke permissions from all the apps you don't use or trust:
https://t.co/lXxCgdnaXH
Online quizzes and such sites often ask for permission to post tweets for you, read your tweets, and even your DMs!.
People click "OK" without reading the fine print.
But imagine the security and privacy risk with having some unknown entity be able to post tweets and read your private DMs just to post the results of what Game of Thrones character you are.
I just completed "Rain Risk" - Day 12 - Advent of Code 2020 https://t.co/0wRPluJVeL #AdventOfCode
Today I learned that I really need coffee ☕️ to operate properly. Made a trivial mistake and it took me forever to catch it. This would have been obv. with a statically typed lang.
Also, I'm using a notebook-style env. to play (like https://t.co/JgFUNSSRuD, here it's https://t.co/XrswSxjjwk). My take away from this fun experience + observations at work is that such notebooks are poison to the mind, fostering bad practices while not bringing much value.
I get that notebooks provide a nice environment for tutorials - you get a literate programming + a printf-debugger on steroids, which is very useful when suffering through tensor shape mismatch errors. It's useful for data science or ML 101.
But then I see people using Python notebooks to do actual work and it's horrifying to me. The natural tendency is to write notebooks as a series of cells mutating global state. So each cell has an implicit API defined by its interaction with the global state. 2/9
The API is implicitly a function of cell exec order, but then you can purposely (or mistakenly) exec cells in any order 😬. And this is on top of the usual issues you get with dynamically typed languages. No one can write maintainable code this way, but notebooks get a pass. 3/9
Today I learned that I really need coffee ☕️ to operate properly. Made a trivial mistake and it took me forever to catch it. This would have been obv. with a statically typed lang.
Also, I'm using a notebook-style env. to play (like https://t.co/JgFUNSSRuD, here it's https://t.co/XrswSxjjwk). My take away from this fun experience + observations at work is that such notebooks are poison to the mind, fostering bad practices while not bringing much value.
I get that notebooks provide a nice environment for tutorials - you get a literate programming + a printf-debugger on steroids, which is very useful when suffering through tensor shape mismatch errors. It's useful for data science or ML 101.
But then I see people using Python notebooks to do actual work and it's horrifying to me. The natural tendency is to write notebooks as a series of cells mutating global state. So each cell has an implicit API defined by its interaction with the global state. 2/9
The API is implicitly a function of cell exec order, but then you can purposely (or mistakenly) exec cells in any order 😬. And this is on top of the usual issues you get with dynamically typed languages. No one can write maintainable code this way, but notebooks get a pass. 3/9
It's interesting (and mildly embarrassing) how much I used to think this too. Holy fuckola, how wrong I was.
Don't get me wrong, our storage engine is the rock upon which everything rests.
As the market matures over the next few years, our strategy and differentiation will shift away from "only we deliver o11y" to exploiting all the unusual capabilities of our storage tier. 😈🐝
Subsecond ad hoc querying over weeks of webscale traffic.. unsampled? ✅
Drill down from high level SLOs to see all of the dimensions, diffed in order of their degree of outlieriness vs the baseline? ✅
The raw speed and flexibility unlocks soooooo many product daydreams.
But that's just good engineering. How to build a product that helps our customers achieve meaningful observability...that is a design problem.
Teaching people to lean into their curiosity and follow the signal? Design (and product) problem.
This time last year, we were hiring our first product leader, our very first design leader. We had ~9 people writing code.
We've been busy 🙃 we now have four in product, seven in design, and just doubled our engineering firepower. Every single one of them is ✨😍amazing 🔥🤩🐝
Huh? How is Honeycomb not exactly that, a managed platform for their custom DB?
— onefuncman (@onefuncman) December 9, 2020
Don't get me wrong, our storage engine is the rock upon which everything rests.
As the market matures over the next few years, our strategy and differentiation will shift away from "only we deliver o11y" to exploiting all the unusual capabilities of our storage tier. 😈🐝
Subsecond ad hoc querying over weeks of webscale traffic.. unsampled? ✅
Drill down from high level SLOs to see all of the dimensions, diffed in order of their degree of outlieriness vs the baseline? ✅
The raw speed and flexibility unlocks soooooo many product daydreams.
But that's just good engineering. How to build a product that helps our customers achieve meaningful observability...that is a design problem.
Teaching people to lean into their curiosity and follow the signal? Design (and product) problem.
This time last year, we were hiring our first product leader, our very first design leader. We had ~9 people writing code.
We've been busy 🙃 we now have four in product, seven in design, and just doubled our engineering firepower. Every single one of them is ✨😍amazing 🔥🤩🐝