Kernel and BIOS updates for the machine itself.
Information Security Framework, Pt I: the Basics:
Let's start with the simple things.
1. Keeping up-to-date on all things software-related on the machine should be paramount.
Not just operating system updates though.
Kernel and BIOS updates for the machine itself.
Keep in mind, some updates on the BIOS itself aren't always necessary.
2. Next, let's talk about things that may communicate over the local network or within a short proximity, such as Bluetooth, airdrop, etc.
If you're not using them, turn them off.
Regardless of what it is, these passwords should be complex enough for an automated brute force-like password attack or dictionary attack.
The next issue people tend to have is using the same password for most accounts.
IF an APT (Advanced Persistent threat) is ran on a large company, such as things we've seen in the last five years, they may be able to retrieve the email AND password of that account.
If they know your email and a common password you use, they can start trying it across the board, going to common sites where folks do business at.
By taking advantage of this opening, they could gather even more info on you, whether that be addresses, birth dates, or even connections to other accounts with significant PII (Personally Identifiable Information).
Simple. Use a password manager.
There are two good options: Keepass and Bitwarden.
Bitwarden is cloud-based, Keepass is not. I personally prefer Keepass as the cloud is a risky place for anything, regardless of how 'secure' they claim they are.
More from Internet
Many conversations happening on #WhatsApp (WA) groups about new #WhatsAppPrivacyPolicy .
This thread has arguments to help ditch WA & move to @signalapp:
https://t.co/En4fe9VxUN
Share, use, copy-paste, modify with understanding as you deem fit on any platform in whole or part
1/n
Note: No affiliations, conflict of interest
Info presented with NO bias, prejudice, malice or indemnity.
Open to corrections: individual tweets may be deleted, tweets added to thread or corrected as replies.
Points that are unclear or uncertain are marked with "(?)".
2/n
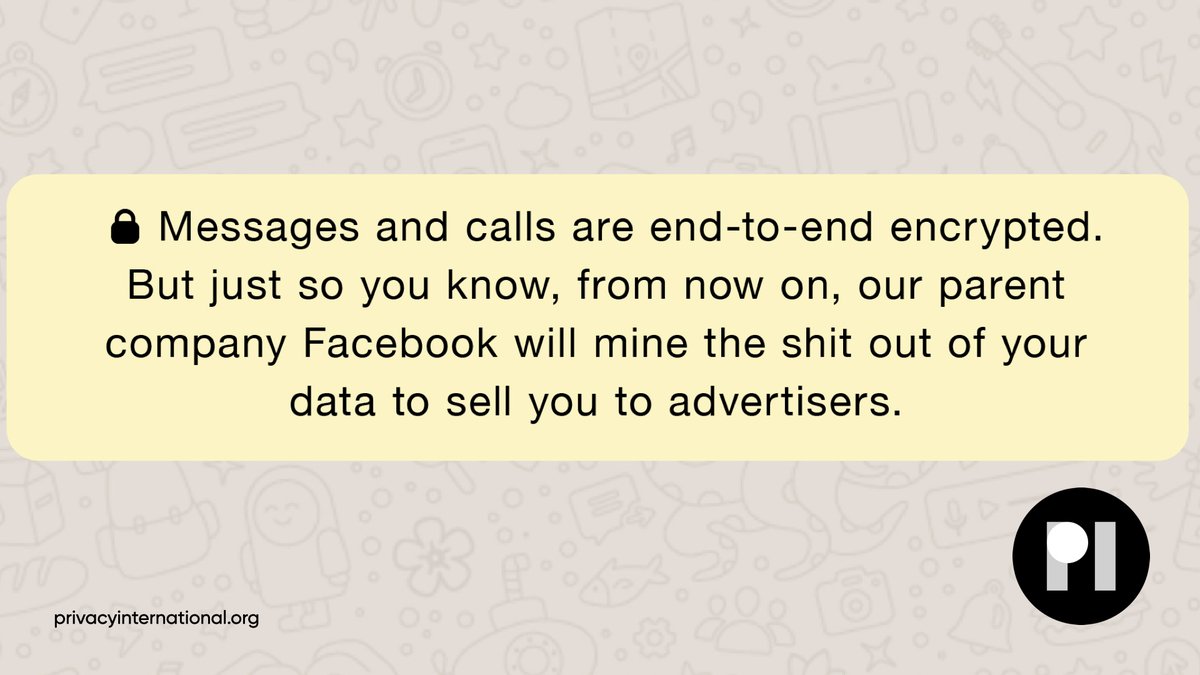
CONTENT OF WA MESSAGES SHALL REMAIN ENCRYPTED END TO END.
BUT, there's data: contacts, group affiliations, co-affiliations, locations (live?), frequency of contacts, *tags* generated when we send or forward a message or file to contacts or groups, links, clicks on links, etc.
3/n
It is unclear whether this data is anonymized.
NOTHING in latest policy *prevents* the collection, retention, sharing or sale by FaceBook (FB: owner of WA) of this data in part or whole whether with identifying information or anonymized.
Meme source:
https://t.co/nMDTUlb0rl
4/n
Companies need to make money & generate profits:
To create software, install & maintain infrastructure.
Google, FB, Insta, Amazon etc sell data created from our content & data generated from our interactions (searches, clicks, purchases etc).
This makes many uncomfortable.
5/n
This thread has arguments to help ditch WA & move to @signalapp:
https://t.co/En4fe9VxUN
Share, use, copy-paste, modify with understanding as you deem fit on any platform in whole or part
1/n
Note: No affiliations, conflict of interest
Info presented with NO bias, prejudice, malice or indemnity.
Open to corrections: individual tweets may be deleted, tweets added to thread or corrected as replies.
Points that are unclear or uncertain are marked with "(?)".
2/n
CONTENT OF WA MESSAGES SHALL REMAIN ENCRYPTED END TO END.
BUT, there's data: contacts, group affiliations, co-affiliations, locations (live?), frequency of contacts, *tags* generated when we send or forward a message or file to contacts or groups, links, clicks on links, etc.
3/n
It is unclear whether this data is anonymized.
NOTHING in latest policy *prevents* the collection, retention, sharing or sale by FaceBook (FB: owner of WA) of this data in part or whole whether with identifying information or anonymized.
Meme source:
https://t.co/nMDTUlb0rl
4/n

Now that #WhatsApp have updated their terms, forcing users to share their data with #Facebook, here's our suggested update to that notification you see at the top of your chats.#WhatsappNewPolicy #WhatsappPrivacy pic.twitter.com/FjxFGBm6Q8
— Privacy International (@privacyint) January 7, 2021
Companies need to make money & generate profits:
To create software, install & maintain infrastructure.
Google, FB, Insta, Amazon etc sell data created from our content & data generated from our interactions (searches, clicks, purchases etc).
This makes many uncomfortable.
5/n
Or, you could let us know when you figure out why it was trending yesterday and the users are complaining which is why Vice wrote about it. Why I'm saying what I am.
There's an assumption here that this problem is fixed bc it was already hacked.
It's not.
We have ppl freezing and dying in TX right now because some ppl who thought they were really smart never spoke to anyone with actual experience with energy systems in extreme cold climates.
Texans are waiting for a solution to a preventable problem.
Farmers are saying that now, not during a crisis, they have to wait for a JD tech to arrive to help them.
The assumption that bc SOME farmers said screw this and used hacked firmware to get around that obstacle doesn't mean that all farmers are doing that.
If all farmers were using hacked firmware we wouldn't be discussing this right now would we?
Of course no one has pointed out that another issue here is that no one at John Deere has figured out they don't have enough staff to quickly and reliably SOLVE problems.
The locked firmware is just one of many issues here.
By not giving people a fast solution they're causing this and other issues.
So what I'm saying is somebody at John Deere needs to examine all of this.
There's an assumption here that this problem is fixed bc it was already hacked.
It's not.
Let us know when you've found the supply chain hack that's already there
— SleeplessOrphan (@sleeplessorphan) February 20, 2021
We have ppl freezing and dying in TX right now because some ppl who thought they were really smart never spoke to anyone with actual experience with energy systems in extreme cold climates.
Texans are waiting for a solution to a preventable problem.
Farmers are saying that now, not during a crisis, they have to wait for a JD tech to arrive to help them.
The assumption that bc SOME farmers said screw this and used hacked firmware to get around that obstacle doesn't mean that all farmers are doing that.
If all farmers were using hacked firmware we wouldn't be discussing this right now would we?
Of course no one has pointed out that another issue here is that no one at John Deere has figured out they don't have enough staff to quickly and reliably SOLVE problems.
The locked firmware is just one of many issues here.
By not giving people a fast solution they're causing this and other issues.
So what I'm saying is somebody at John Deere needs to examine all of this.
You May Also Like
"I really want to break into Product Management"
make products.
"If only someone would tell me how I can get a startup to notice me."
Make Products.
"I guess it's impossible and I'll never break into the industry."
MAKE PRODUCTS.
Courtesy of @edbrisson's wonderful thread on breaking into comics – https://t.co/TgNblNSCBj – here is why the same applies to Product Management, too.
There is no better way of learning the craft of product, or proving your potential to employers, than just doing it.
You do not need anybody's permission. We don't have diplomas, nor doctorates. We can barely agree on a single standard of what a Product Manager is supposed to do.
But – there is at least one blindingly obvious industry consensus – a Product Manager makes Products.
And they don't need to be kept at the exact right temperature, given endless resource, or carefully protected in order to do this.
They find their own way.
make products.
"If only someone would tell me how I can get a startup to notice me."
Make Products.
"I guess it's impossible and I'll never break into the industry."
MAKE PRODUCTS.
Courtesy of @edbrisson's wonderful thread on breaking into comics – https://t.co/TgNblNSCBj – here is why the same applies to Product Management, too.
"I really want to break into comics"
— Ed Brisson (@edbrisson) December 4, 2018
make comics.
"If only someone would tell me how I can get an editor to notice me."
Make Comics.
"I guess it's impossible and I'll never break into the industry."
MAKE COMICS.
There is no better way of learning the craft of product, or proving your potential to employers, than just doing it.
You do not need anybody's permission. We don't have diplomas, nor doctorates. We can barely agree on a single standard of what a Product Manager is supposed to do.
But – there is at least one blindingly obvious industry consensus – a Product Manager makes Products.
And they don't need to be kept at the exact right temperature, given endless resource, or carefully protected in order to do this.
They find their own way.































