As the @nytimes team shows, his security entourage featured a host of #OathKeepers...
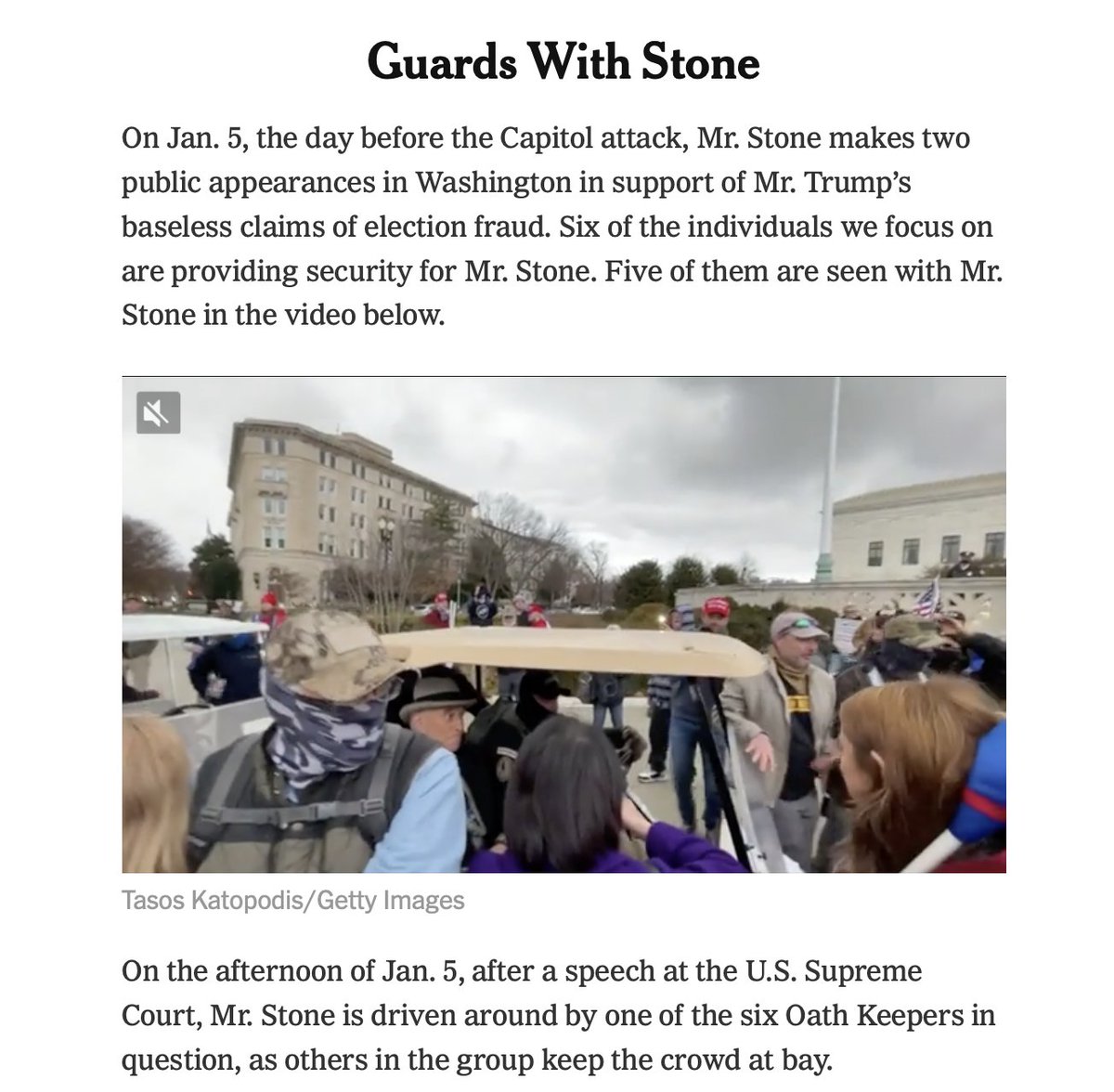



NEW: Rob Minuta guarded Roger Stone Jan 6th...& was later seen at #Capitol siege..
— John Scott-Railton (@jsrailton) February 7, 2021
Now we know he has a history of escorting Trump allies like Flynn & Alex Jones. Also seen in December w/indicted Proud Boy #Spazzo.
THREAD
By @arawnsley
Link: https://t.co/8t38iOmgYP pic.twitter.com/dnRYZGuBCO


Here's the footage of Roberto Minuta throwing a tantrum at the police, 1/6 at the east side of the Capitol (5:16 in the Youtube video link).
— Capitol Terrorists Exposers (@CTExposers) February 10, 2021
\u27a1\ufe0fhttps://t.co/rulMuaftCm pic.twitter.com/wz6A4zQLYT

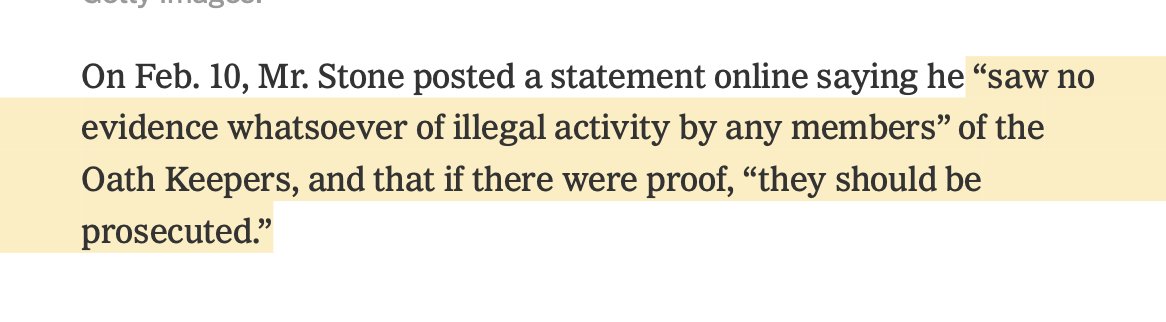
"I never left my hotel room at all on January 6"
— John Scott-Railton (@jsrailton) February 8, 2021
- Roger Stone to @VICE news' @misstessowen
Stone was, of course, filmed outside on the 6th..\U0001f447
Quote source: https://t.co/phpZc0ZrPfhttps://t.co/uAeLFns8lRhttps://t.co/vPH0Ald1o0 pic.twitter.com/GCiZVHBXJx


This is the last time Mr. Stone is seen on Jan. 6 in any footage we reviewed. However, it's worth pointing out that \u2014on Gab, Telegram and Twitter\u2014 Mr. Stone continues promoting speeches and rallies that he says will happen near the Capitol that afternoon. But he never appears. pic.twitter.com/p64JN1Hg6H
— Christiaan Triebert (@trbrtc) February 14, 2021
Last but not least, it's worth pointing out that, after they exited the Capitol, all six individuals who provided security to Roger Stone on Jan. 5 and 6 gathered around Stewart Rhodes, the founder of the Oath Keepers: https://t.co/mAKhKZ25zI
— Christiaan Triebert (@trbrtc) February 14, 2021
Battle of the Bulge
— JeLove (@LovesTheLight) December 22, 2020
1226
44
101
BB https://t.co/NkaSAyGiCa
"You called down the thunder? Well now you got it."
— JeLove (@LovesTheLight) January 16, 2021
"You tell'em the laws coming....and hells coming with me"
Its a Day of Reckoning.
3:16
42https://t.co/ty1hgfL7iV pic.twitter.com/aczIsLUrX0
The stock exploded & went up as much as 63% from my price.
— Manas Arora (@iManasArora) June 22, 2020
Closed my position entirely today!#BroTip pic.twitter.com/CRbQh3kvMM
What an extended (away from averages) move looks like!!
— Manas Arora (@iManasArora) June 24, 2020
If you don't learn to sell into strength, be ready to give away the majority of your gains.#GLENMARK pic.twitter.com/5DsRTUaGO2
#HIKAL
— Manas Arora (@iManasArora) July 2, 2021
Closed remaining at 560
Reason: It is 40+% from 10wma. Super extended
Total revenue: 11R * 0.25 (size) = 2.75% on portfolio
Trade closed pic.twitter.com/YDDvhz8swT
When you see 15 green weeks in a row, that's the end of the move. *Extended*
— Manas Arora (@iManasArora) August 26, 2019
Simple price action analysis.#Seamecltd https://t.co/gR9xzgeb9K
Ironies of Luck https://t.co/5BPWGbAxFi
— Morgan Housel (@morganhousel) March 14, 2018
"Luck is the flip side of risk. They are mirrored cousins, driven by the same thing: You are one person in a 7 billion player game, and the accidental impact of other people\u2019s actions can be more consequential than your own."