(the stripe report is here: https://t.co/SbyZDarWr9)
Developer productivity, y'all. It is a three TRILLION dollar opportunity, per the stripe report.
Eng managers and directors, we have got to stop asking for "more headcount" and start treating this like the systems problem that it is. https://t.co/XJ0CkFdgiO
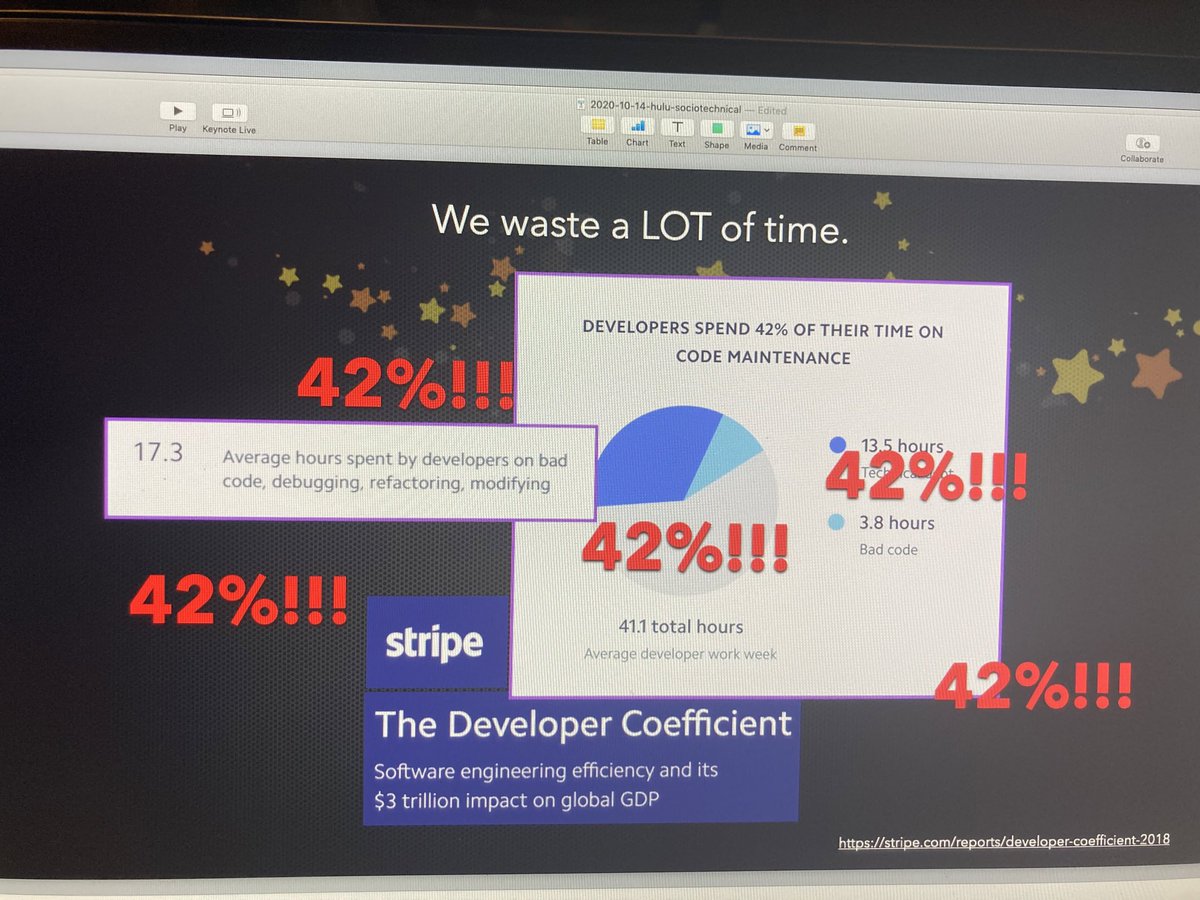
When people often have to spend weeks just to get a local development environment up, there is a lot to improve. \U0001f641
— Daniel Schildt (@autiomaa) December 20, 2020
(the stripe report is here: https://t.co/SbyZDarWr9)
By my calculations, that would reclaim 3 engineers worth of capacity given a team of just 17-18 people.
But also, we are wasting a fuck load of people's valuable time and energy, all because we refuse to improve our pipeline and fulfill the real promise of Continuous Delivery.
But it's not. It's the brutal grind of detangling stupid problems that should never have existed, repeatedly, with your eyes taped closed.
It's getting woken up in the middle of the night. It's flappy pages. For deprecated code.
And let us be clear: this is a fucking management problem. The fact that developer productivity is not high on every VP, director, and manager 2021 goals is a management failure.
You've seen this graph, right? (The yellow bubble is the "elite" teams.)
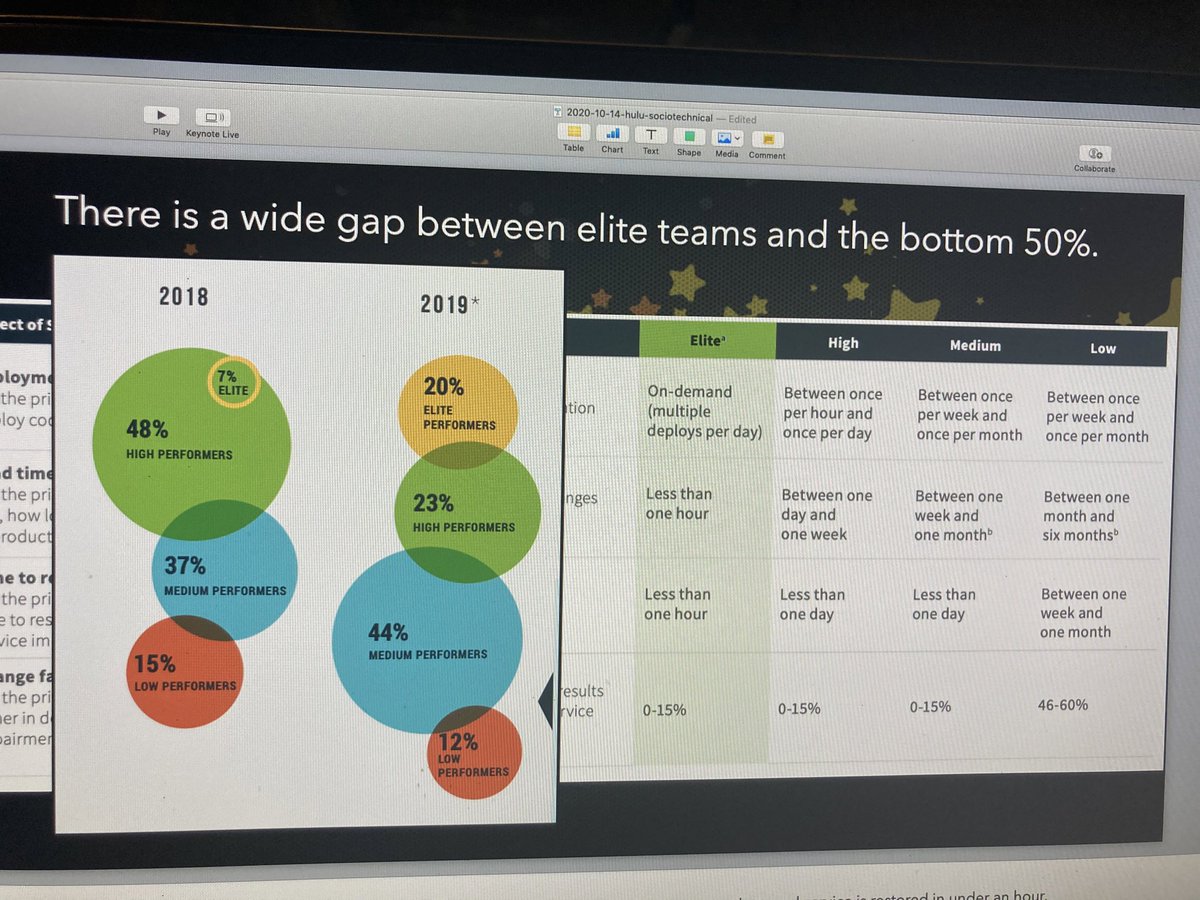
Then they tend to that shit, and don't let it drift.
I am sure there are exceptions, but increasingly I see this as a manager/director/VP eng problem.
Hear me out. I don't have it out for y'all; I've known some stellar nontech EMs.
That's a hard line for an EM to take with upper management (none of whom may have read or care about DORA reports or Accelerate).
EMs who don't have that personal grounded knowledge? Nah. I can't imagine going out on this limb based on hearsay. I sure wouldn't.
Anyone who walls you off with people OR tech isn't acting in your interest long term.
Moral of the story? (Morals?)
If you are an engineer, set yourself a goal that 2020 is the last year you leak time working for a place without observability and CD. Find one or help your job become one, but don't get left behind.
(If you *don't* know...catch up I guess)
The power to change the lives of engineers and teams around the world *dramatically* for the better rests primarily with you.
You span worlds. You have the moral authority of the doer and the influence.
But what is the point of power and influence if you don't haul it out when a mountain needs moving?
This fucking mountain, lol. Burn it to the grond. 😈
More from Software
As the year wrap's up, let's run through some of the worst public security mistakes and delays in fixes by AWS in 2020. A thread.
First, that time when an AWS employee posted confidential AWS customer information including including AWS access keys for those customer accounts to
Discovery by @SpenGietz that you can disable CloudTrail without triggering GuardDuty by using cloudtrail:PutEventSelectors to filter all events.
Amazon launched their bug bounty, but specifically excluded AWS, which has no bug bounty.
Repeated, over and over again examples of AWS having no change control over their Managed IAM policies, including the mistaken release of CheesepuffsServiceRolePolicy, AWSServiceRoleForThorInternalDevPolicy, AWSCodeArtifactReadOnlyAccess.json, AmazonCirrusGammaRoleForInstaller.
First, that time when an AWS employee posted confidential AWS customer information including including AWS access keys for those customer accounts to
Fresh data breach news-
— Chris Vickery (@VickerySec) January 23, 2020
Amazon AWS engineer exposes work-related keys, passwords, and documents marked "Amazon Confidential" via public Github repository: https://t.co/7gkIegnslx
Discovered within 30 minutes of exposure by my team at @UpGuard.
Discovery by @SpenGietz that you can disable CloudTrail without triggering GuardDuty by using cloudtrail:PutEventSelectors to filter all events.
"Disable" most #AWS #CloudTrail logging without triggering #GuardDuty:https://t.co/zVe4uSHog9
— Rhino Security Labs (@RhinoSecurity) April 23, 2020
Reported to AWS Security and it is not a bug.
Amazon launched their bug bounty, but specifically excluded AWS, which has no bug bounty.
Amazon Vulnerability Research Program - Doesn't include AWS D:https://t.co/stJHDG68pj#BugBounty #AWS
— Spencer Gietzen (@SpenGietz) April 22, 2020
Repeated, over and over again examples of AWS having no change control over their Managed IAM policies, including the mistaken release of CheesepuffsServiceRolePolicy, AWSServiceRoleForThorInternalDevPolicy, AWSCodeArtifactReadOnlyAccess.json, AmazonCirrusGammaRoleForInstaller.
You May Also Like
Nano Course On Python For Trading
==========================
Module 1
Python makes it very easy to analyze and visualize time series data when you’re a beginner. It's easier when you don't have to install python on your PC (that's why it's a nano course, you'll learn python...
... on the go). You will not be required to install python in your PC but you will be using an amazing python editor, Google Colab Visit https://t.co/EZt0agsdlV
This course is for anyone out there who is confused, frustrated, and just wants this python/finance thing to work!
In Module 1 of this Nano course, we will learn about :
# Using Google Colab
# Importing libraries
# Making a Random Time Series of Black Field Research Stock (fictional)
# Using Google Colab
Intro link is here on YT: https://t.co/MqMSDBaQri
Create a new Notebook at https://t.co/EZt0agsdlV and name it AnythingOfYourChoice.ipynb
You got your notebook ready and now the game is on!
You can add code in these cells and add as many cells as you want
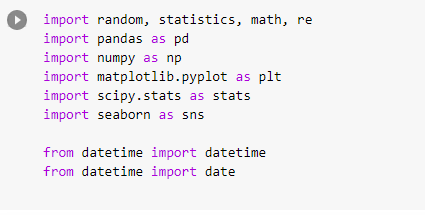
# Importing Libraries
Imports are pretty standard, with a few exceptions.
For the most part, you can import your libraries by running the import.
Type this in the first cell you see. You need not worry about what each of these does, we will understand it later.
==========================
Module 1
Python makes it very easy to analyze and visualize time series data when you’re a beginner. It's easier when you don't have to install python on your PC (that's why it's a nano course, you'll learn python...
... on the go). You will not be required to install python in your PC but you will be using an amazing python editor, Google Colab Visit https://t.co/EZt0agsdlV
This course is for anyone out there who is confused, frustrated, and just wants this python/finance thing to work!
In Module 1 of this Nano course, we will learn about :
# Using Google Colab
# Importing libraries
# Making a Random Time Series of Black Field Research Stock (fictional)
# Using Google Colab
Intro link is here on YT: https://t.co/MqMSDBaQri
Create a new Notebook at https://t.co/EZt0agsdlV and name it AnythingOfYourChoice.ipynb
You got your notebook ready and now the game is on!
You can add code in these cells and add as many cells as you want
# Importing Libraries
Imports are pretty standard, with a few exceptions.
For the most part, you can import your libraries by running the import.
Type this in the first cell you see. You need not worry about what each of these does, we will understand it later.



























