https://t.co/TKh2CR1vFW
"The leaked email communication from an executive of #Stratfor says that, as Deputy National Security Advisor in 2010 to #Obama, #Brennan and the White House were determined to:
'go after anyone printing materials negative to the Obama agenda.'"
#NoCPTPP
'#Brennan is behind the #witchhunts of investigative journalists learning information from inside the beltway sources...'"
https://t.co/TKh2CR1vFW
https://t.co/TKh2CR1vFW
https://t.co/TKh2CR1vFW
https://t.co/TKh2CR1vFW
https://t.co/TKh2CR1vFW
https://t.co/TKh2CR1vFW
https://t.co/TKh2CR1vFW
#TPPIsABackDoorDeal4China
#NoTPP #StopCPTPP
"'It was all a massive conflict of interest, and it was all a bit weird,' a former employee said. 'I believe the Chinese thought we were working for the #CIA.'"
https://t.co/95vqN6v0Ln
https://t.co/HDECsBbBpR
2+, almost killed
1 impeached
2 threatened w/extradition
1 in exile
1 media outlet branded "Russian agent"
1 capitulated to DNC, now parrots phony Russiagate speech, despite being a victim of it.
3+ smeared & careers harmed.
https://t.co/yp61lGqPWN
I've updated a list of BIPARTISAN/INTERNATIONAL #StopTPP #activists to show pattern of who was targeted by phony #Russiagate.#NoTPP #StopTPP #NoCPTPP #StopCPTPP pic.twitter.com/NulAbh1xqN
— \u23f3Elizabeth Mueller\u231b\ufe0f (@LizActivate) November 30, 2020
#HunterBiden accepted $ from #China in 2011, same yr #Biden Sr met w/China to discuss #FakeTradeDeals, like #TPP--now "#CPTPP."
— \u23f3Elizabeth Mueller\u231b\ufe0f (@LizActivate) November 30, 2020
After #JulianAssange published TPP text to warn public & #Trump withdrew USA from TPP--Stop TPP groups targeted by #Russiagate. https://t.co/VssFphkxf6 https://t.co/yp61lGqPWN pic.twitter.com/xwZOYVYCws
"Covert actions" can be ordered by President, with Congressional approval.
— \u23f3Elizabeth Mueller\u231b\ufe0f (@LizActivate) November 30, 2020
Military & DoD can also perform similar actions.
(OPE)
"loss of life" & U.S. sponsorship can be concealed?!
Fuck that noise.
Rip open #Russiagate docs--declassify them all.https://t.co/1eK0TS9MPH pic.twitter.com/cCr9T5NqUd
Get ALL of #JohnBrennan's classified documents for phony #Russiagate. Break them WIDE OPEN. Find all the #targets...announce them. Find all the sec people assigned to harm targets. Indict. Them. All.
— \u23f3Elizabeth Mueller\u231b\ufe0f (@LizActivate) September 25, 2020
-->#GetThem https://t.co/Dr8sHZTYJy
More from Crime
*sigh*
talk about "lizard people," David Ickes, QAnon, and the extreme antisemitism lurking like a rabid Loch Ness monster in this soup of conspiracy.
Trumpist lawyer Lin Wood, who I believe has petitions pending before the Supreme Court, is in the middle of a flurry of tweets alleging Chief Justice John Roberts murdered a child on video. Also something about a Lizard Squad and assassins and, well, lots of stuff. pic.twitter.com/EPbeQLyDIk
— Helen Kennedy (@HelenKennedy) January 4, 2021
You May Also Like
(I am forced to do this due to continuous hounding of Sikh Extremists since yesterday)
Rani Jindan Kaur, wife of Maharaja Ranjit Singh had illegitimate relations with Lal Singh (PM of Ranjit Singh). Along with Lal Singh, she attacked Jammu, burnt - https://t.co/EfjAq59AyI

Tomorrow again same thing happens bcoz fudus like you are creating a narrative oh Khalistan. when farmers are asking MSP. (RSS ki tatti khane wale Kerni sena ke kutte).
— Ancient Economist (@_stock_tips) December 5, 2020
U kill sikhs in 1984 just politics. To BC low IQ fudu Saale entire history was politics.
Hindu villages of Jasrota, caused rebellion in Jammu, attacked Kishtwar.
Ancestors of Raja Ranjit Singh, The Sansi Tribe used to give daughters as concubines to Jahangir.

The Ludhiana Political Agency (Later NW Fronties Prov) was formed by less than 4000 British soldiers who advanced from Delhi and reached Ludhiana, receiving submissions of all sikh chiefs along the way. The submission of the troops of Raja of Lahore (Ranjit Singh) at Ambala.
Dabistan a contemporary book on Sikh History tells us that Guru Hargobind broke Naina devi Idol Same source describes Guru Hargobind serving a eunuch
YarKhan. (ref was proudly shared by a sikh on twitter)
Gobind Singh followed Bahadur Shah to Deccan to fight for him.

In Zafarnama, Guru Gobind Singh states that the reason he was in conflict with the Hill Rajas was that while they were worshiping idols, while he was an idol-breaker.
And idiot Hindus place him along Maharana, Prithviraj and Shivaji as saviours of Dharma.

This New York Times feature shows China with a Gini Index of less than 30, which would make it more equal than Canada, France, or the Netherlands. https://t.co/g3Sv6DZTDE
That's weird. Income inequality in China is legendary.
Let's check this number.
2/The New York Times cites the World Bank's recent report, "Fair Progress? Economic Mobility across Generations Around the World".
The report is available here:
3/The World Bank report has a graph in which it appears to show the same value for China's Gini - under 0.3.
The graph cites the World Development Indicators as its source for the income inequality data.
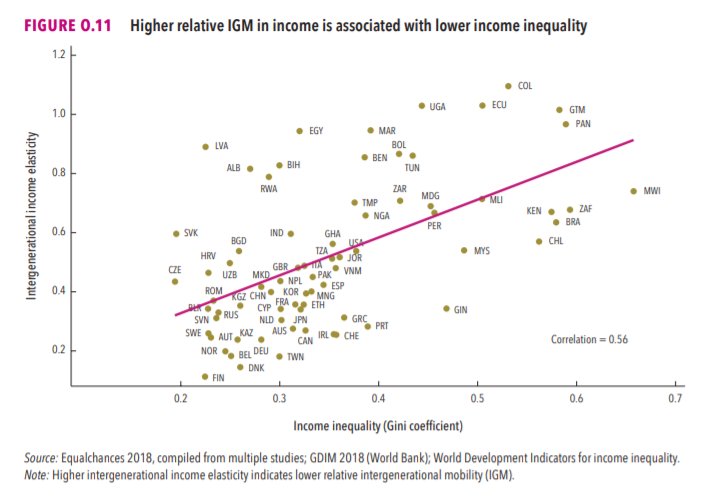
4/The World Development Indicators are available at the World Bank's website.
Here's the Gini index: https://t.co/MvylQzpX6A
It looks as if the latest estimate for China's Gini is 42.2.
That estimate is from 2012.
5/A Gini of 42.2 would put China in the same neighborhood as the U.S., whose Gini was estimated at 41 in 2013.
I can't find the <30 number anywhere. The only other estimate in the tables for China is from 2008, when it was estimated at 42.8.
Viruses and other pathogens are often studied as stand-alone entities, despite that, in nature, they mostly live in multispecies associations called biofilms—both externally and within the host.
https://t.co/FBfXhUrH5d

Microorganisms in biofilms are enclosed by an extracellular matrix that confers protection and improves survival. Previous studies have shown that viruses can secondarily colonize preexisting biofilms, and viral biofilms have also been described.

...we raise the perspective that CoVs can persistently infect bats due to their association with biofilm structures. This phenomenon potentially provides an optimal environment for nonpathogenic & well-adapted viruses to interact with the host, as well as for viral recombination.

Biofilms can also enhance virion viability in extracellular environments, such as on fomites and in aquatic sediments, allowing viral persistence and dissemination.